Security groups act as virtual firewalls for Elastic Compute Service (ECS) instances. By managing security groups and their rules, you can implement fine-grained network security, fencing, and access control.
The following figure shows an example scenario. Two security group rules are configured to allow only authorized IP addresses to remotely manage an instance and to block the instance from accessing high-risk sites on the internet.
Inbound rule: Allows a specific IP address (
121.XX.XX.XX) to access the instance through the Secure Shell Protocol (SSH) (port 22).Outbound rule: Denies the instance access to a known high-risk IP address (
XX.XX.XX.XX).

Configure a security group for a new instance
Go to the instance purchase page: Go to the ECS console - Custom Launch page and select the instance configurations.
Create a new security group: In the Network & Security section, create a basic security group or an enterprise security group and edit its name.
Quickly configure common rules: When you purchase an instance, the console provides common ports and protocols. You can select the checkboxes to allow traffic from all IP addresses (
0.0.0.0/0) to the destination ports or to allow traffic that follows the specified protocols to access the instance.
You cannot configure fine-grained rules for a security group when you create it during the instance purchase. You can configure the rules after the instance is created. If you select ports for instance management, such as the common remote connection ports SSH (22) or RDP (3389), during the quick configuration, you must configure the security group rules to allow access only from secure IP addresses after the instance is created.
Modify, add, or delete security group rules after creation: After you purchase an instance, you can use the information in Security group rules to add, modify, or delete security group rules for the new instance.
For information about how to configure security group rules for various business scenarios, such as restricting instance access and defining database security policies, see Security Group Application Guide and Examples.
Manage security groups
You can modify the rules of a security group after it is created with an ECS instance. You can also create and manage security groups independently and then associate them with existing ECS instances.
Create a security group
Console
Go to the ECS console - Security Groups page and click Create Security Group.
Set the security group name and Virtual Private Cloud.
For the Security group type, select Basic Security Group or Enterprise Security Group.
After you add security group rules, click OK.
API
Call CreateSecurityGroup to create a security group.
If no rules are configured for a newly created basic security group, it allows traffic from other ECS instances within the same security group by default, denies all other inbound traffic, and allows all outbound traffic.
Add, modify, or delete security group rules
A security group rule defines the conditions that network traffic must meet to be allowed inbound to or outbound from a security group. When you configure a rule, you must specify parameters such as the traffic direction, destination, and priority. Because security group rules are stateful, you only need to configure an inbound rule, and the security group automatically allows the corresponding outbound response traffic.
Console
Go to the ECS console - Security Groups page and click the ID of the target security group to open its details page.
Configure security group rules.
Add a rule: On the details page of the target security group, select a rule direction and click Add Rule.
Modify a rule: On the details page of the target security group, locate the destination rule in the Rules area and click Edit in the Actions column.
Delete a rule: On the details page of the security group, in the Rules area, find the rule to delete and click Delete in the Actions column.
API
Call AuthorizeSecurityGroup to add an inbound rule.
Call AuthorizeSecurityGroupEgress to add an outbound rule.
Call ModifySecurityGroupRule to modify the inbound rule.
Call ModifySecurityGroupEgressRule to modify the outbound rule.
Call RevokeSecurityGroup to delete the inbound rule.
Call RevokeSecurityGroupEgress to delete an outbound rule.
At the same priority level, deny rules take precedence. For some specific network traffic, security groups allow the traffic by default.
To reduce security risks in your production environment, configure security group rules based on the principle of least privilege (whitelist). Avoid allowing access from all sources (do not use 0.0.0.0/0 or ::/0) for high-risk scenarios such as logging on to or managing ECS instances.
Avoid modifying security groups in a production environment directly. You can first clone a security group, test the changes in a staging environment, and ensure that instance traffic is normal. Then, you can modify the security group rules in the production environment.
Associate a security group with an instance
When you associate a security group with an ECS instance, you are actually associating the security group with the primary network interface controller (NIC) of the ECS instance.
Console
Go to the ECS console - Instances page and click the ID of the target instance to open its details page.
On the instance details page, switch to the Security Groups tab and click Change Security Groups to add or remove a security group for the instance. If multiple security groups are associated with the instance, their rules are merged and applied in order of priority.
API
Call ModifyInstanceAttribute to set multiple security groups for an ECS instance.
Call JoinSecurityGroup to add an ECS instance to a specified security group.
Call LeaveSecurityGroup to remove an ECS instance from a specified security group.
Associate a security group with a secondary ENI
Security groups are applied to the Elastic Network Interfaces (ENIs) of an ECS instance. If an instance has multiple ENIs, you can associate different security groups with the ENIs and configure different security group rules to implement granular control and service isolation for internal network traffic.
Console
Go to the ECS console - Elastic Network Interfaces page and click the ID of the target secondary ENI to open its details page.
Click Change Security Groups, select the security groups to associate, and click OK.
API
Call JoinSecurityGroup to add an elastic network interface (ENI) to a specified security group.
Call LeaveSecurityGroup to remove an elastic network interface from a specified security group.
You can use ModifyNetworkInterfaceAttribute to specify multiple security groups for an elastic network interface.
Use prefix lists
To grant access to multiple IP address segments, use prefix lists for centralized management. This simplifies security group rule configuration and improves batch maintenance efficiency.
Console
Create a prefix list:
Go to ECS console - Prefix List.
Select the target tab as needed, and then click Create Prefix List.
For a security group that references a prefix list, the number of rules is calculated based on the maximum number of entries set for the list.
In the Rules section on the details page of the target security group, add or modify a rule:
Set Source to Prefix List and then select the target prefix list.
API
Call CreatePrefixList to create a prefix list. After the list is created, call DescribePrefixListAttributes to query the details of the prefix list.
Call AuthorizeSecurityGroup to add an inbound rule that grants access from a prefix list by setting the SourcePrefixListId parameter.
Call AuthorizeSecurityGroupEgress to add an outbound rule that grants access to a prefix list by setting the DestPrefixListId parameter.
Clone a security group
When you need to create multiple security groups with the same configuration in batches, or perform cross-region or cross-network type replication and backup, you can use the Clone Security Group feature. After a successful clone, the new security group appears in the security group list of the destination region.
Go to Security Groups and click Clone Security Group in the Operation column of the target security group.
Configure the destination security group. The new security group appears in the security group list of the destination region after it is cloned.
VPC ID: The network type for the new security group. Select the classic network or a specific VPC.
Retention Rule: Select this option to retain all rules in the original security group. Rules with a priority greater than 100 are adjusted to 100.
Copy Tags of Current Security Group: Select whether to copy the tags from the source security group to the new security group.
Check for redundant rules
The security group health check feature can detect redundant rules. A rule (Rule A) is redundant if its conditions are completely covered by another rule (Rule B) and its priority is not higher than the priority of Rule B. Redundant rules consume the security group rule quota. You should remove them periodically to avoid being unable to add new rules because the rule limit is reached.
Go to ECS console - Security groups. On the details page of the target security group, in the Rules section, click Health Check.
In the Health Check dialog box, select the redundant rules and click Are you sure that you want to delete the preceding monitoring rules.
Import or export rules
You can use the import and export features to back up, recover, or migrate rules.
Import rules
Imported security group rules must meet the following requirements:
File format: JSON or CSV.
Number of rules: A maximum of 200 rules can be imported at a time.
Rule priority: 1 to 100. Rules with a priority higher than 100 are ignored.
When you import rules across regions, security group rules that authorize security groups or prefix lists are not supported. Security group rules that specify port lists for the port range are also not supported.
Go to ECS console - Security Group. On the security group details page, go to the Rules section and click Import Security Group Rule.
On the Import Security Group Rule page, click Select File, select a local JSON or CSV file, and click Confirm.
If the import fails, hover over the warning icon to view the reason.
Export rules
Go to ECS console - Security Groups. On the target security group's product page, click Export in the Rules area. The exported rule file is named in the following format:
JSON format: ecs_${region_id}_${groupID}.json.
Example: If the Region ID is
cn-qingdaoand the security group ID issg-123, the exported file is namedecs_cn-qingdao_sg-123.json.CSV format: ecs_sgRule_${groupID}_${region_id}_${time}.csv.
Example: If the Region ID is
cn-qingdao, the security group ID issg-123, and the export date is2020-01-20, the exported file is namedecs_sgRule_sg-123_cn-qingdao_2020-01-20.csv.
Security group snapshots
Security group snapshots can automatically back up security group rules. When a security group rule changes, the system automatically creates a snapshot. You can use snapshots to recover security group rules from a specific point in time to prevent rule loss due to accidental operations.
After a security group rule changes, the system creates a snapshot after 5 minutes. If multiple changes occur within 5 minutes, the system creates only one snapshot based on the rules before the first change.
Security group snapshots use Object Storage Service (OSS) to store backup data. OSS is a pay-as-you-go service. Using security group snapshots incurs corresponding OSS storage and request fees.
Create a snapshot policy
On the Security Group Snapshots page, click Create Security Group Snapshot Policy.
In the Create Security Group Snapshot Policy dialog box, configure the following settings:
Policy Name: Enter a name for the snapshot policy.
Policy Status: The status of the policy. Valid values are Enable and Disable. Snapshots are created for the associated security groups only if the policy is enabled.
Snapshot Retention Period: The number of days to retain snapshots. The value can be from 1 to 30 days, with a default of 1 day. Snapshots are automatically deleted after the retention period expires.
OSS Storage Configuration: Specifies the OSS bucket for storing snapshot data. If a bucket is not specified, the system uses the default bucket.
Click OK.
When you create a snapshot policy for the first time, the system prompts you to grant the service-linked role (SLR)
ALIYUNSECURITYGROUPSNAPSHOTROLEpermission to access the OSS bucket. If this role already exists, you do not need to grant the permission again.
Associate a security group with a snapshot policy
After you create a snapshot policy, you must associate it with a security group to start backing up the security group rules.
When you associate a security group with a snapshot policy, the system immediately creates a snapshot for that security group.
Go to ECS console - Security Group Snapshots, find the target snapshot policy, and click Associate Security Group in the Actions column.
In the Bind Security Group dialog box, select the security groups.
A snapshot policy can be associated with up to 10 security groups. A security group can be associated with multiple snapshot policies that have different policies.
Click Confirm to complete the association.
Recover rules from a snapshot
The recovery operation takes effect immediately. All current rules are completely overwritten by the rules in the snapshot. The recovery cannot be undone.
Go to the ECS console - Security Groups page and click the ID of the target security group to open its details page.
On the security group details page, switch to the Snapshots tab, and in the Actions column for the target snapshot, click Restore Snapshot.
In the Restore Security Group dialog box, confirm the restore details.
On the Inbound and Outbound tabs, you can compare the Current Security Group Rules with the Restored Security Group Rules.
Confirm that the information is correct and click OK.
Delete a security group
Deleting a security group is an irreversible operation that permanently deletes all rules in the security group. Before you perform this operation, make sure to back up the relevant configurations.
Console
Go to ECS Console - Security Group and click Delete in the Operation column of the target security group.
In the Delete Security Group dialog box, confirm the details and click Confirm.
If the security group is not associated with any ECS instances or elastic network interfaces (ENIs), but the Delete Security Group dialog box still displays Non-deletable, you can click Force-delete.
API
Call DeleteSecurityGroup to delete a security group.
A security group cannot be deleted in the following scenarios:
It is associated with an ECS instance or ENI. You must remove the association first.
It is authorized by another security group rule. You must delete the authorization rule first.
Managed security groups are view-only and cannot be deleted.
Deletion protection is enabled. Disable deletion protection and then try again. If you cannot disable deletion protection, you cannot delete the security group.
If you receive the
InvalidOperation.DeletionProtectionerror code when you call the DeleteSecurityGroupDeletion Protection message in the console, this indicates that deletion protection is enabled for the security group.
Network communication between instances in a security group
By default, ECS instances within the same basic security group can communicate with each other over the internal network. To improve security, you can change the internal connectivity policy to internal isolation to prohibit internal network communication between instances.
Enterprise security groups do not support modifying the internal access policy.
If an instance is associated with multiple security groups, the instances can communicate with each other over the internal network as long as the internal connectivity policy of any of the security groups is set to allow internal communication.
If the internal connectivity policy of a security group is set to internal isolation, you can configure security group rules to allow communication between instances.
Console
Go to the ECS console - Security Groups page and click the ID of the target security group to open its details page.
In the Basic Information section on the Security Group Details page, click Modify Internal Access Control Policy.
The internal network connectivity policy for the security group is set to Internal Isolation.
API
Call the ModifySecurityGroupPolicy operation to modify the intra-group connectivity policy of a basic security group.
Network communication between instances in different security groups
When you set another security group as the authorization object in a rule, you can allow instances in the other security group to access instances in the current security group over the internal network. For example, in the figure, after Security Group B is set as the authorization object for an inbound rule of Security Group A, instances in Security Group B can access instances in Security Group A over the internal network.
Enterprise security group rules do not support adding rules where the authorization object is a security group.
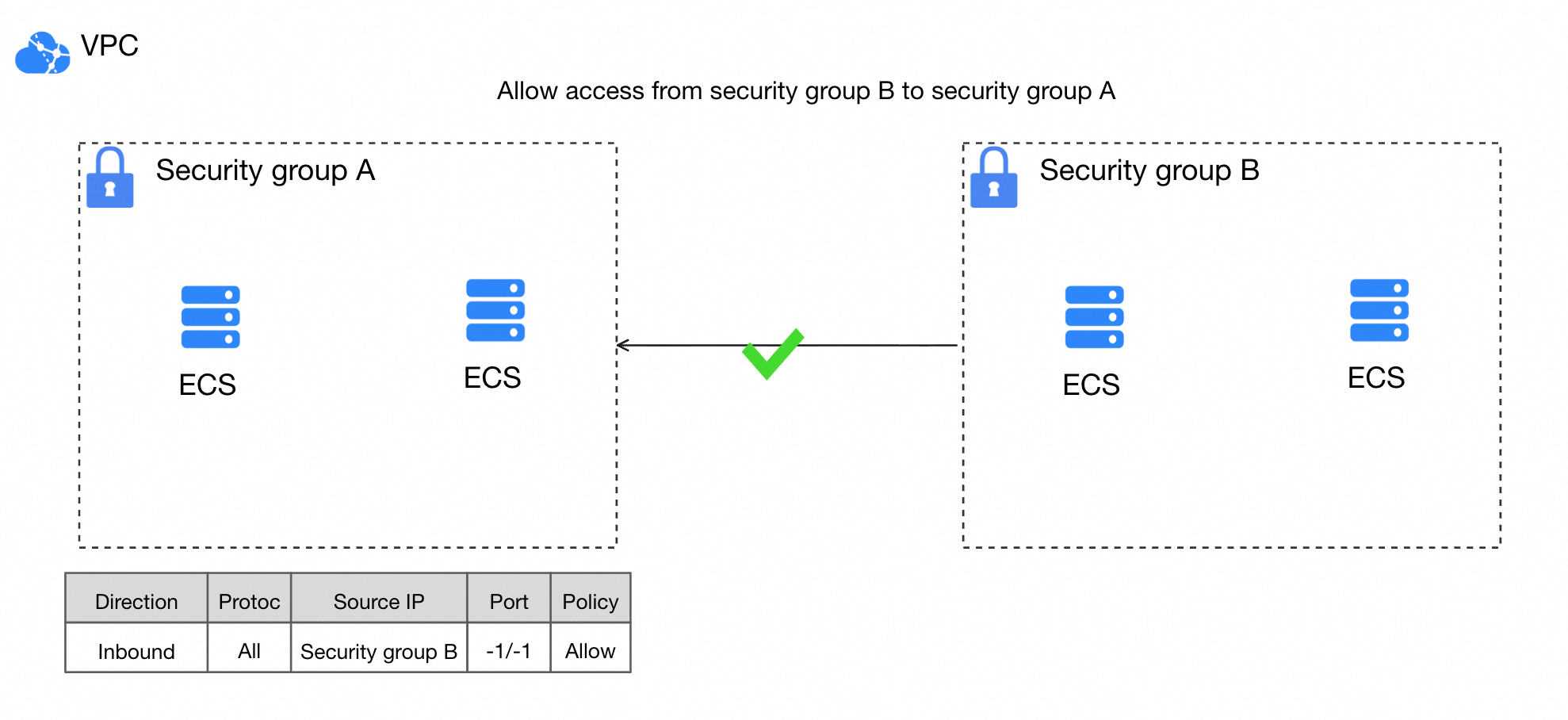
Console
Go to the ECS console - Security Groups page and click the ID of the target security group to open its details page.
On the target Security Group Details page, select the rule direction and click Add Rule.
On the Create Security Group Rule page, set Source to Security Group or Cross-account Security Group.
API
Call AuthorizeSecurityGroup to set `SourceGroupId` in a security group inbound rule to authorize the created security group.
Call AuthorizeSecurityGroupEgress to set the DestGroupId in an outbound rule of the security group to grant permissions to the created security group.
Production application recommendations
Security group planning
Single responsibility: Use separate security groups for different business scenarios, such as web, database, and cache services.
Environment isolation: Keep security groups for production and staging environments separate. Do not mix them.
Naming convention: Use the format
environment-application-purpose-sg, such asprod-mysql-db-sg.
Rule configuration
Least privilege: Open only necessary ports to necessary sources. Avoid opening management ports such as SSH (22) and RDP (3389) to
0.0.0.0/0. Always restrict access to trusted, fixed IP addresses.Default deny: Deny all inbound traffic by default. Add inbound rules to allow access from specific ports and sources only when necessary.
Rule priority conflicts: When an instance is associated with multiple security groups, a low-priority allow rule is overwritten by a high-priority deny rule. When troubleshooting network connectivity issues, check all associated security groups.
Change management
Avoid directly modifying the production environment: Directly modifying a security group in a production environment is a high-risk operation. First, clone the security group and test it in a staging environment. After you confirm that instance traffic is normal, you can modify the security group rules in the production environment.
Billing rules
Security groups are free of charge.
Limits
Limit item | Basic security group limits | Enterprise security group limits |
Maximum number of security groups per Alibaba Cloud account in a region | Use the quota ID | Same as basic security groups |
Number of security groups that can be associated with a single Elastic Network Interface (ENI) | 10 | Same as basic security groups |
Maximum total number of rules (inbound and outbound) for all security groups associated with a single ENI | 1,000 | Same as basic security groups |
Number of rules in a single security group where the authorization object is another security group | 20 | 0. In an enterprise security group, you cannot add rules where the authorization object is another security group. You also cannot use an enterprise security group as the authorization object in other security group rules. |
Number of VPC-type ECS instances that a single VPC-type security group can contain | Not fixed. The number is affected by the number of private IP addresses the security group can contain. | Unlimited |
Number of private IP addresses that a single VPC-type security group can contain for a single Alibaba Cloud account in a specific region | 6,000 Note
| 65,536 Note The number of used IP addresses represents the total number of ENIs associated with a security group, including both primary and secondary network interfaces of an instance. |
Public access port | For security reasons, port 25 of ECS instances is restricted by default. Use a Secure Sockets Layer (SSL) encrypted port, usually port 465, to send emails. | Same as basic security groups |
FAQ
What do I do if I cannot ping an instance?
What do I do if I cannot connect to an instance or access a service?
What is the difference between security groups and network ACLs (NACLs)?
How do I change or add a security group for the primary NIC of an instance?
After setting a security group rule to deny all, how do I allow access from internal Alibaba Cloud services?
References
How to prevent RAM users from creating high-risk security group rules
Automatically auditing and remediating security group rule compliance
Troubleshoot remote connection issues with your Windows instance
Troubleshoot ineffective security group rules for an ECS instance
Troubleshoot a failure to ping the public IP address of an ECS instance