This topic describes how to upgrade from Red Hat Enterprise Linux (RHEL) 7 to RHEL 8 or from RHEL 8 to RHEL 9 on an Elastic Compute Service (ECS) instance.
Upgrade from RHEL 7 to RHEL 8
After June 30, 2024, RHEL 7 transitioned from the Maintenance Support phase to the Extended Life phase. After that, Red Hat provides limited technical support for RHEL 7. For comprehensive technical support and security updates, we recommend that you upgrade from RHEL 7 to RHEL 8.
If you want to continue using RHEL 7.9, including security updates and bug fixes for this version, we recommend that you purchase an Alibaba Cloud Red Hat Enterprise Linux Extended Life Cycle Support (ELS) Add-on subscription. For more information, see the Purchase a RHEL 7 ELS Add-on subscription section of the "Red Hat Enterprise Linux" topic.
Prerequisites
The ECS instance that you want to upgrade can run RHEL 8. For more information, see Red Hat Enterprise Linux Technology Capabilities and Limits.
The ECS instance that you want to upgrade uses a RHEL 7 public image that is purchased from Alibaba Cloud and contains a RHEL 7 license or uses a RHEL 7 image that is imported to Alibaba Cloud and contains a separately purchased Alibaba Cloud RHEL 7 license.
NoteAn Alibaba Cloud RHEL license provides legal permissions to access RHEL software, security updates, and technical support when you use RHEL in Alibaba Cloud.
If you purchased a RHEL 7 operating system from Red Hat, visit the Red Hat website for information about how to upgrade from RHEL 7 to RHEL 8.
Procedure
Before you upgrade from RHEL 7 to RHEL 8, we recommend that you understand the risks of the upgrade and create snapshots to back up data. This ensures that you can restore data when an upgrade issue occurs.
Connect to the ECS instance that runs RHEL 7 as the root user.
For more information, see Use Workbench to connect to a Linux instance over SSH.
ImportantThe upgrade involves modifications to system configuration and library files. Root permissions are required to ensure that the upgrade can be completed as expected.
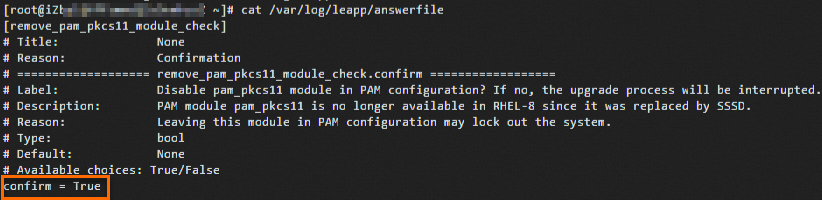
Run the following command to check whether the ECS instance has an Alibaba Cloud RHEL 7 license.
rpm -q client-rhel7If no information is returned, the ECS instance does not have an Alibaba Cloud RHEL 7 license. In this case, purchase a license before you upgrade the operating system.
If the returned output is similar to
client-rhel7-3.0-1.el7_9.noarch, the ECS instance has an Alibaba Cloud RHEL 7 license. You can proceed to the subsequent steps.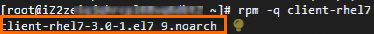
Prepare the RHEL 7 operating system for the upgrade.
Run the following commands to upgrade the operating system to the latest version available in the current repository, which contains fixes for known vulnerabilities, bugs, and security risks, and restart the operating system for the upgrade to take effect:
yum -y update rebootRun the following command to install the Leapp utility in the RHEL operating system:
yum -y install leapp leapp-rhui-alibaba --enablerepo="*"Run the following command to check whether the Leapp utility is installed:
leapp --versionIf the returned output is similar to
leapp version xxx, the Leapp utility is installed.
Perform a pre-upgrade check.
Due to the differences among RHEL versions, you must use the Leapp utility to perform a pre-upgrade check. You can view the check results and modify the configurations as needed based on the suggestions for upgrade.
Perform a pre-upgrade check.
Run the following command to pre-upgrade to the latest version of RHEL 8:
leapp preupgrade --no-rhsmRun the following command to pre-upgrade to a specific RHEL 8 version, such as an upgrade from RHEL 7 to RHEL 8.8:
leapp preupgrade --no-rhsm --target 8.8NoteTo view the supported RHEL 8 versions, run the
leapp preupgrade -hcommand.
View the pre-upgrade check results.
Leapp pre-upgrade check logs are stored in the following log files:
/var/log/leapp/leapp-preupgrade.log: stores the logs of the Leapp utility.
/var/log/leapp/leapp-report.txt: stores the pre-upgrade check report in the text format.
/var/log/leapp/leapp-report.json: stores the pre-upgrade check report in the JSON format.
If the pre-upgrade check fails, specific failed items are displayed as shown in the following figure.
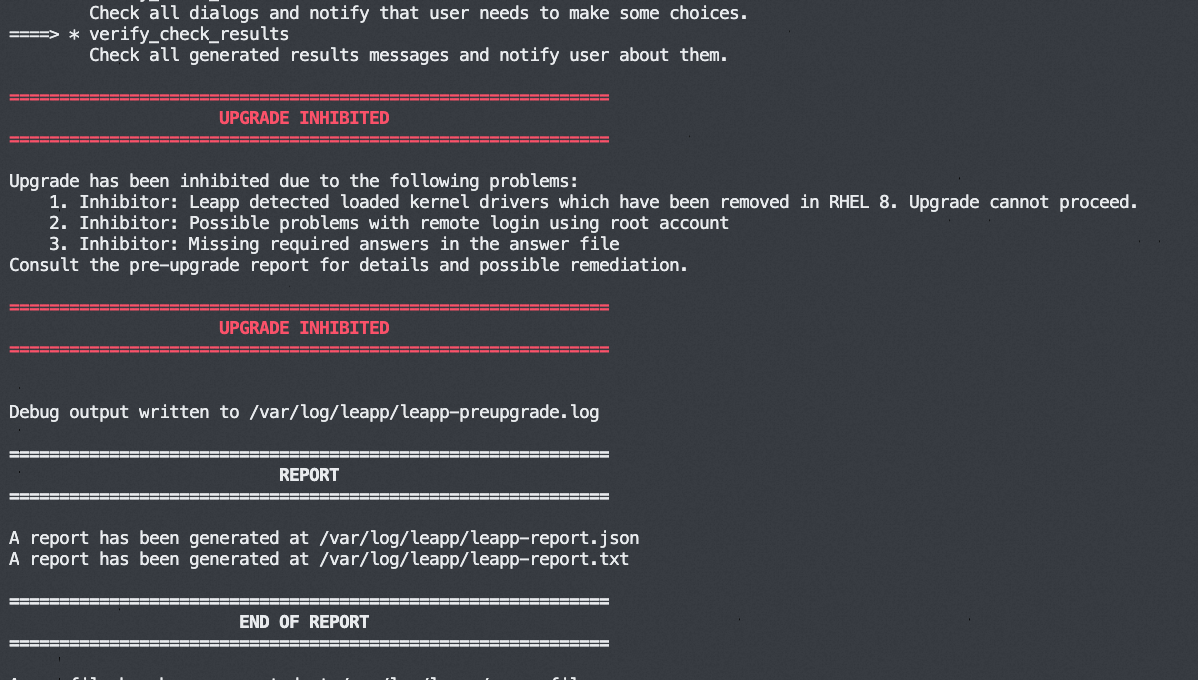
(Conditionally required) Resolve pre-upgrade issues.
Check the
/var/log/leapp/leapp-report.txtlog file for pre-upgrade issues and resolve the issues based on the suggestions of the Leapp utility. The following section describes some common pre-upgrade issues and their solutions by risk level.high (inhibitor): high-risk inhibitors. Issues of this level directly block the upgrade and must be resolved before the upgrade can proceed.
high: high-risk issues. Issues of this level do not directly block the upgrade. However, we recommend that you resolve the issues before or after the upgrade to prevent post-upgrade exceptions.
medium: medium-risk issues. Issues of this level do not directly block the upgrade. However, we recommend that you resolve the issues before or after the upgrade to eliminate potential issues after the upgrade.
low: low-risk issues. Issues of this level have minor impacts on the upgrade or system operation. However, we recommend that you resolve the issues before or after the upgrade to ensure stable system operation.
info: informational prompts. In most cases, issues of this level do not affect the upgrade or system operation. You can review the prompts in the report to obtain the changes during the upgrade.
Upgrade from RHEL 7 to RHEL 8.
Run the following command to upgrade to the latest version of RHEL 8:
leapp upgrade --no-rhsmRun the following command to upgrade to a specific RHEL 8 version, such as an upgrade from RHEL 7 to RHEL 8.8:
leapp upgrade --no-rhsm --target 8.8
The following command output indicates that the upgrade is complete.
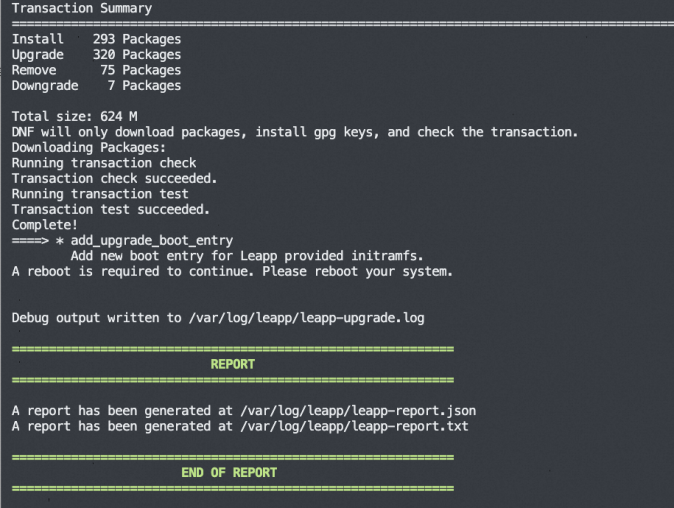
Run the following command to restart the ECS instance:
rebootVerify the upgrade result.
Run the
cat /etc/redhat-releasecommand to check whether the operating system version is upgraded.Check the upgrade logs or report.
Check whether your business runs as expected on RHEL 8.
(Conditionally required) Run the following commands to configure the RHEL 8 software repository.
After the upgrade, the
/etc/dnf/vars/releaseverfile is modified by default to specify the RHEL 8 version you used in the preceding steps. For example, the RHEL 8 repository address is set tohttps://xxxx/8.8/xxx, and you can access only RHEL 8.8 software packages. If you want to have automatic access to packages of the latest minor version of RHEL 8, delete the releasever configuration file and rebuild the metadata cache. This way, you can obtain the latest security patches and feature updates.rm -f /etc/dnf/vars/releasever dnf clean all && dnf makecacheAfter the preceding commands are run, the RHEL 8 repository address is updated to
https://xxxx/8/xxx. Then, the operating system can automatically obtain the latest RHEL 8 security patches and feature updates to ensure that it is always up-to-date.
Upgrade from RHEL 8 to RHEL 9
Although RHEL 8 is still in the Full Support phase, you can upgrade from RHEL 8 to RHEL 9 for the latest features, hardware adaptations, and long-term support.
Prerequisites
The ECS instance that you want to upgrade can run RHEL 9. For more information, see Red Hat Enterprise Linux Technology Capabilities and Limits.
The ECS instance that you want to upgrade uses a RHEL 8 public image that is purchased from Alibaba Cloud and contains a RHEL 8 license or a RHEL 8 image that is imported to Alibaba Cloud and contains a separately purchased Alibaba Cloud RHEL 8 license.
NoteAn Alibaba Cloud RHEL license provides legal permissions to access RHEL software, security updates, and technical support when you use RHEL in Alibaba Cloud.
If you purchased a RHEL 8 operating system from Red Hat, visit the Red Hat website for information about how to upgrade from RHEL 8 to RHEL 9.
Procedure
Before you upgrade from RHEL 8 to RHEL 9, we recommend that you understand the risks of the upgrade and create snapshots to back up data. This ensures that you can restore data when an upgrade issue occurs.
Connect to the ECS instance that runs a RHEL 8 operating system as the root user.
For more information, see Use Workbench to connect to a Linux instance over SSH.
ImportantThe upgrade involves modifications to system configuration and library files. Root permissions are required to ensure that the upgrade can be completed as expected.
Run the following command to check whether the ECS instance has an Alibaba Cloud RHEL 8 license:
rpm -qa |grep aliyunIf no information is returned, the ECS instance does not have an Alibaba Cloud RHEL 8 license. In this case, purchase a license before you upgrade the operating system.
If the command output contains a minor version, such as
rhel8.6, submit a ticket to obtain and install the latest Red Hat Package Manager (RPM) package before you upgrade the operating system to RHEL 9. Note
NoteTo run a RHEL operating system in Alibaba Cloud, the operating system must access the Red Hat software repository by using Alibaba Cloud Red Hat Update Infrastructure (RHUI). If a minor version, such as
aliyun_rhel8.6-2.0-1.noarch, is installed in the operating system, the operating system may fail to connect to RHUI, which prevents it from obtaining software updates or upgrading to a new version.If the command output contains license information, such as
aliyun_rhui_rhel8-2.0-3.x86_64, the ECS instance has an Alibaba Cloud RHEL 8 license. You can proceed to the subsequent steps.
Prepare the RHEL 8 operating system for the upgrade.
Run the following commands to upgrade the operating system to the latest version available in the current repository, which contains fixes for known vulnerabilities, bugs, and security risk, and restart the operating system for the upgrade to take effect:
yum -y update rebootRun the following command to install the Leapp utility in the RHEL operating system:
yum -y install leapp leapp-rhui-alibaba --enablerepo="*"Run the following command to check whether the Leapp utility is installed:
leapp --versionIf a command output similar to
leapp version xxxis returned, the Leapp utility is installed.
Perform a pre-upgrade check.
Due to the differences among RHEL versions, you must use the Leapp utility to perform a pre-upgrade check. You can view the check results and modify the configurations as needed based on the suggestions for upgrade.
Perform a pre-upgrade check.
Run the following command to pre-upgrade to the latest version of RHEL 9:
leapp preupgrade --no-rhsmRun the following command to pre-upgrade to a specific RHEL 9 version, such as an upgrade from RHEL 8 to RHEL 9.4:
leapp preupgrade --no-rhsm --target 9.4NoteTo view the supported RHEL 9 versions, run the
leapp preupgrade -hcommand.
View the pre-upgrade check results.
Leapp pre-upgrade check logs are stored in the following log files:
/var/log/leapp/leapp-preupgrade.log: stores the logs of the Leapp utility.
/var/log/leapp/leapp-report.txt: stores the pre-upgrade check report in the text format.
/var/log/leapp/leapp-report.json: stores the pre-upgrade check report in the JSON format.
If the pre-upgrade check fails, specific failed items are displayed as shown in the following figure.
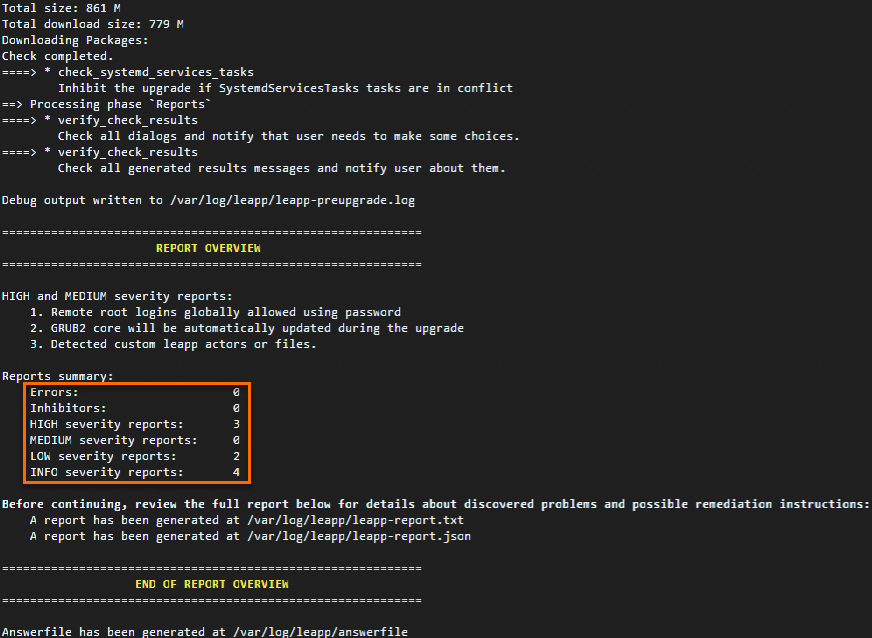
(Conditionally required) Resolve pre-upgrade issues.
Check the
/var/log/leapp/leapp-report.txtlog file for pre-upgrade issues and resolve the issues based on the suggestions of the Leapp utility. The following section describes some common pre-upgrade issues and their solutions by risk level.high: high-risk issues. Issues of this level do not directly block the upgrade. However, we recommend that you resolve the issues before or after the upgrade to prevent post-upgrade exceptions.
low: low-risk issues. Issues of this level have minor impacts on the upgrade process or system operation. However, we recommend that you resolve the issues before or after the upgrade to ensure stable system operation.
info: informational prompts. In most cases, issues of this level do not affect the upgrade or system operation. You can review the prompts in the report to obtain the changes during the upgrade.
Upgrade from RHEL 8 to RHEL 9.
Run the following command to upgrade to the latest version of RHEL 9:
leapp upgrade --no-rhsmRun the following command to upgrade to a specific RHEL 9 version, such as an upgrade from RHEL 8 to RHEL 9.4:
leapp upgrade --no-rhsm --target 9.4
The following command output indicates that the upgrade is complete.

Run the following command to restart the ECS instance:
rebootVerify the upgrade result.
Run the
cat /etc/redhat-releasecommand to check whether the operating system version is upgraded.Check the upgrade logs or report.
Check whether your business runs as expected in RHEL 9.
(Conditionally required) Run the following commands to configure the RHEL 9 software repository.
After the upgrade, the
/etc/dnf/vars/releaseverfile is modified by default to specify the RHEL 9 version you used in the preceding steps. For example, the RHEL 9 repository address is set tohttps://xxxx/9.4/xxx, and you can access only RHEL 9.4 software packages. If you want to have automatic access to packages of the latest minor version of RHEL 9, delete the releasever configuration file and rebuild the metadata cache. This way, you can obtain the latest security patches and feature updates.rm -f /etc/dnf/vars/releasever dnf clean all && dnf makecacheAfter the preceding commands are run, the RHEL 9 repository address is updated to
https://xxxx/9/xxx. Then, the operating system can automatically obtain the latest RHEL 9 security patches and feature updates to ensure that it is always up-to-date.
References
You can also upgrade from RHEL 8 to RHEL 9 by using Server Migration Center (SMC). For more information, see Migrate a Linux operating system.
For more information about RHEL, see Red Hat Enterprise Linux.
For information about the frequently asked questions about the RHEL 7 Extended Life phase, see the FAQ documentation on the Red Hat website.