This topic describes the precise access control feature, and how to enable and configure this feature.
Overview
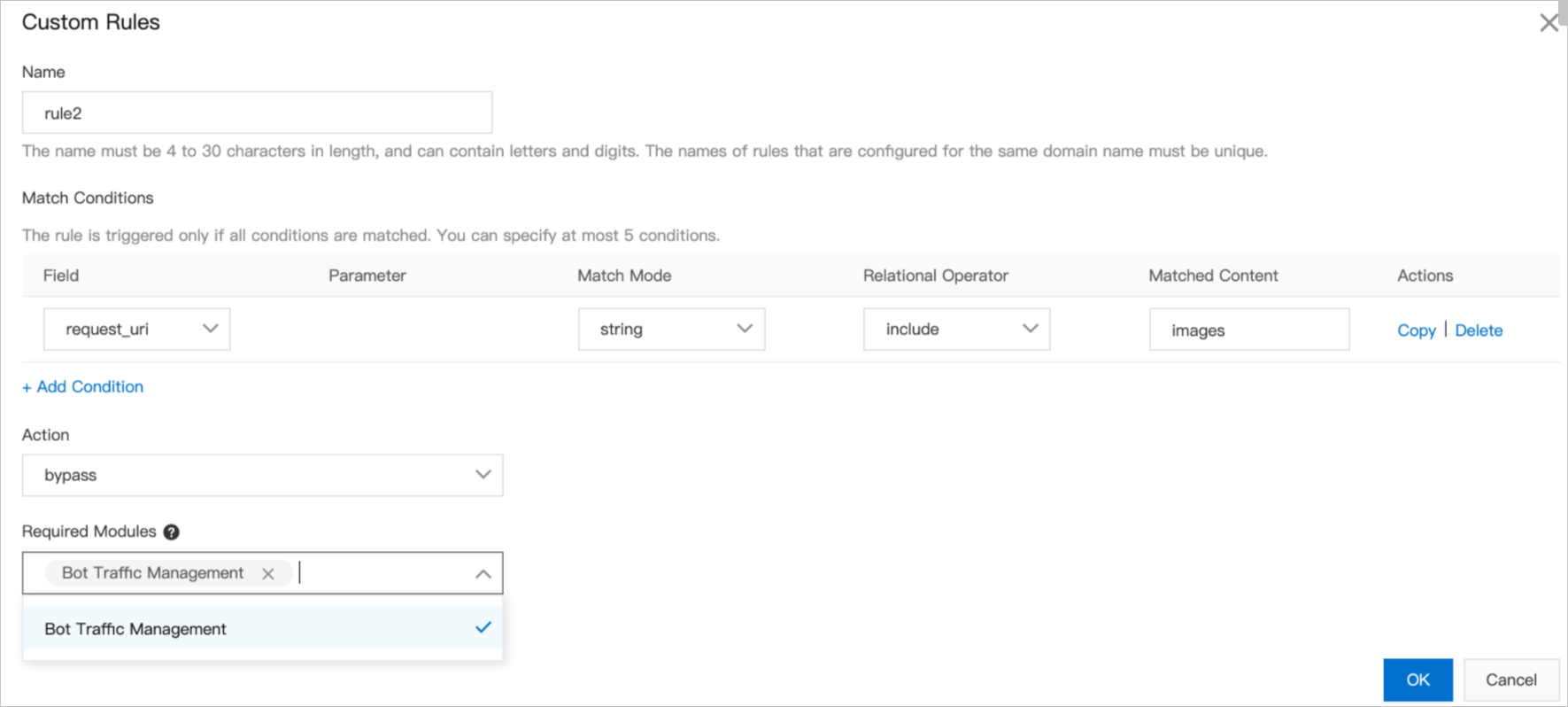
The precise access control feature allows you to add custom match conditions to match user requests and perform specified actions on requests that matches the conditions. Match conditions support common HTTP fields such as IP, URL, and header. You can add different match conditions to meet the protection requirements in different scenarios.
ACL rules
An access control list (ACL) rule consists of one or more match conditions and one action. You can add one or more ACL rules. If you add multiple ACL rules, the rules are listed and matched against requests in descending order of priority. When a rule is matched, the system stops matching subsequent rules.
Enable precise access control
To enable the precise access control feature, visit the Contact Sales page, and leave your contact information. An Alibaba Cloud sales representative will contact you as soon as possible.