You can use GitOps in an ACK One fleet instance to manage applications using Git repositories as the single source of truth. This lets you implement version management, multi-cluster distribution, and continuous deployment for applications that use various orchestration methods, such as YAML manifest directories, Helm charts, and Kustomize. GitOps is fully compatible with the community version of Argo CD and provides a high-availability control plane. This topic describes how to use GitOps in an ACK One fleet instance to deliver applications to multiple clusters and helps you get started.
Prerequisites
The Fleet management feature is enabled.
Multiple clusters are associated with the fleet instance. For more information, see Add an associated cluster.
The AliyunAdcpFullAccess permission is granted to the RAM user. For more information, see Grant permissions to a RAM user.
(Required for the CLI method) You have obtained the kubeconfig file of the fleet instance from the ACK One console and used kubectl to connect to the fleet.
(Required for the CLI method) The latest version of Cloud Assistant CLI is installed and Cloud Assistant CLI is configured.
Billing rules
After you enable GitOps, ACK One creates the following resources by default.
An SLB instance is created to expose the API and UI access endpoints of Argo CD.
A pay-as-you-go ECI instance with 2 vCPUs and 4 GB of memory is created to run the Argo CD service.
For more information about billing, see Billing of cloud resources for multi-cluster fleets.
Supported regions
This feature is available in all regions where the ACK One fleet management feature is enabled. For more information, see Regions that support multi-cluster Fleets and workflow clusters.
Step 1: Enable public access to the GitOps console
The GitOps feature is enabled by default when you create an ACK One fleet instance. You can access the GitOps console through a VPC. To do this, you must connect your on-premises network to the VPC.
To access the GitOps console over the Internet to perform operations, such as submitting and viewing applications, you can follow these steps to enable public access.
Enabling public access poses security risks. Therefore, you must configure an Access Control List (ACL) when you enable public access.
Enable public access in the console
Log on to the ACK One console. In the left-side navigation pane, choose .
On the Multi-cluster GitOps page, click the
 icon next to the fleet name in the upper-left corner and select the destination fleet from the drop-down list.
icon next to the fleet name in the upper-left corner and select the destination fleet from the drop-down list.GitOps is enabled by default for a new fleet. If GitOps is not enabled for your fleet, click Enable GitOps. In the dialog box that appears, click OK.
If GitOps is enabled for the fleet, the GitOps Console button appears on the Multi-cluster GitOps page.
On the Multi-cluster GitOps page, click Enable next to Public Access. In the Enable Public Access dialog box that appears, enter the IP addresses or CIDR blocks that you want to add to the whitelist and click OK.
After the fleet is updated, you can click GitOps Console in the upper-right corner of the page to access the GitOps console over the Internet.
Enable public access using Cloud Assistant CLI
Make sure that you are using the latest version of Cloud Assistant CLI. Then, run the following command to enable GitOps and public access.
Replace
<your_clusterid>with the ID of your fleet instance.Replace the value of
AccessControlListwith the CIDR blocks that you want to add to the whitelist. For more information about how to obtain the CIDR blocks, see Enable public access to Argo CD.
aliyun adcp UpdateHubClusterFeature --ClusterId <your_clusterid> --PublicAccessEnabled true --AccessControlList "[\"10.100.XX.XX/24\"]" --ArgoCDEnabled trueOptional: If you use the AccessKey pair of a RAM user, you must grant the AliyunAdcpFullAccess permission to the RAM user. For more information, see Grant permissions to a RAM user.
Step 2: Create an application in the GitOps console and distribute it to the destination cluster
Deploy an application in the console
On the Multi-cluster GitOps page, click GitOps Console to go to the Argo CD UI logon page. Click LOG IN VIA ALIYUN to log on to the Argo CD UI using Single Sign-On (SSO) with your Alibaba Cloud account.
Connect to a repository.
In the navigation pane on the left of the Argo CD UI, click Settings. Then, choose .
In the panel that appears, configure the following parameters and click CONNECT.
Area
Parameter
Value
Choose your connection method
-
VIA HTTP/HTTPS
CONNECT REPO USING HTTP/HTTPS
Type
git
Project
default
Repository URL
https://github.com/AliyunContainerService/gitops-demo.git
Skip server verification
Select this checkbox.
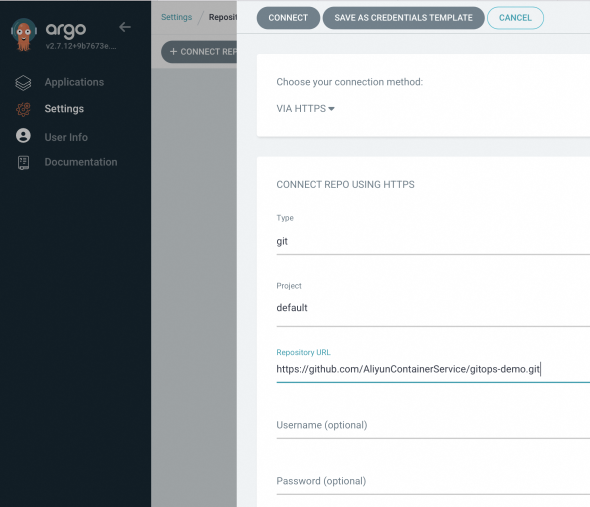
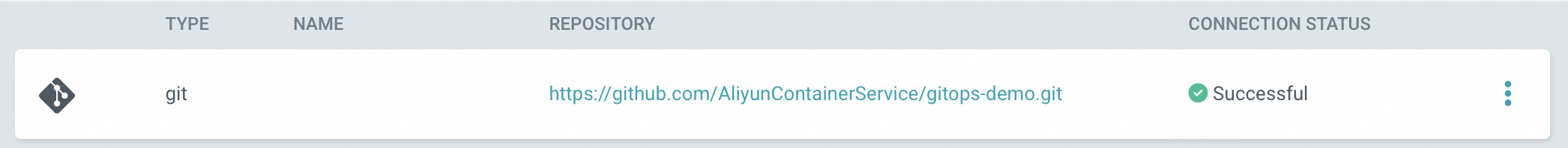
After the repository is connected, the CONNECTION STATUS of the Git repository changes to Successful.
Create an application.
In the navigation pane on the left of the Argo CD UI, choose Applications and then click + NEW APP.
In the panel that appears, configure the following parameters and click CREATE.
Area
Parameter
Value
GENERAL
Application Name
echo-server-demo
Project Name
default
SYNC POLICY
Select Automatic from the drop-down list.
The following options are available:
Manual: If changes are made in the Git repository, you must manually synchronize the changes to the destination cluster.
Automatic: The Argo CD server automatically detects changes in the Git repository every 3 minutes and deploys the changes to the destination cluster.
SYNC OPTIONS
Select AUTO-CREATE NAMESPACE.
SOURCE
Repository URL
Select an existing Git repository from the drop-down list. In this example, https://github.com/AliyunContainerService/gitops-demo.git is selected.
Revision
HEAD
Path
manifests/helm/echo-server
DESTINATION
Cluster URL
Select the destination cluster from the drop-down list.
Namespace
echo-server-demo
HELM
VALUES FILES
values.yaml
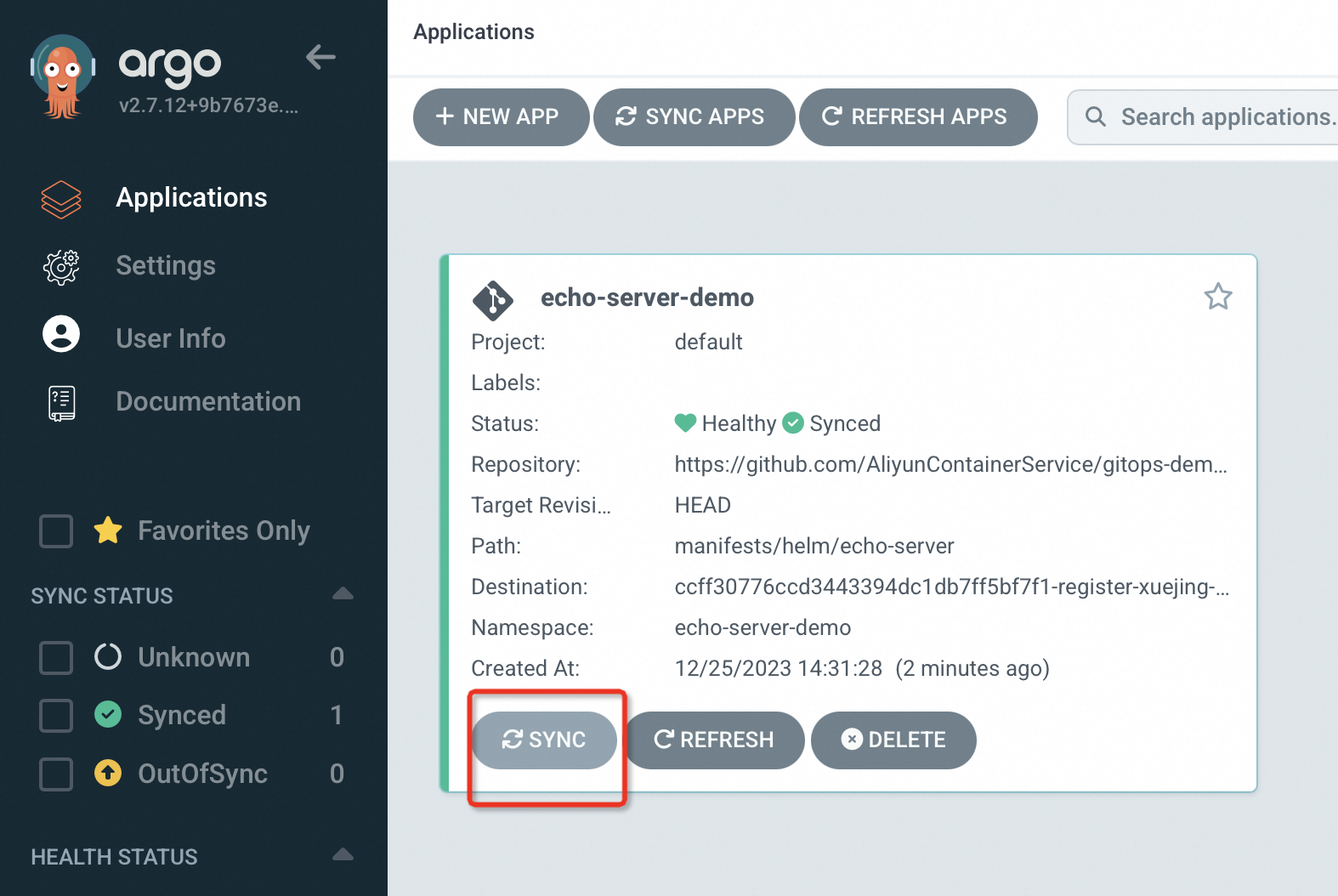
After the application is created, you can view the status of the echo-server-demo application on the Applications page.
If you set SYNC POLICY to Manual, you must click SYNC to synchronize the application to the destination cluster. The application is synchronized when its Status is Healthy and Synced.
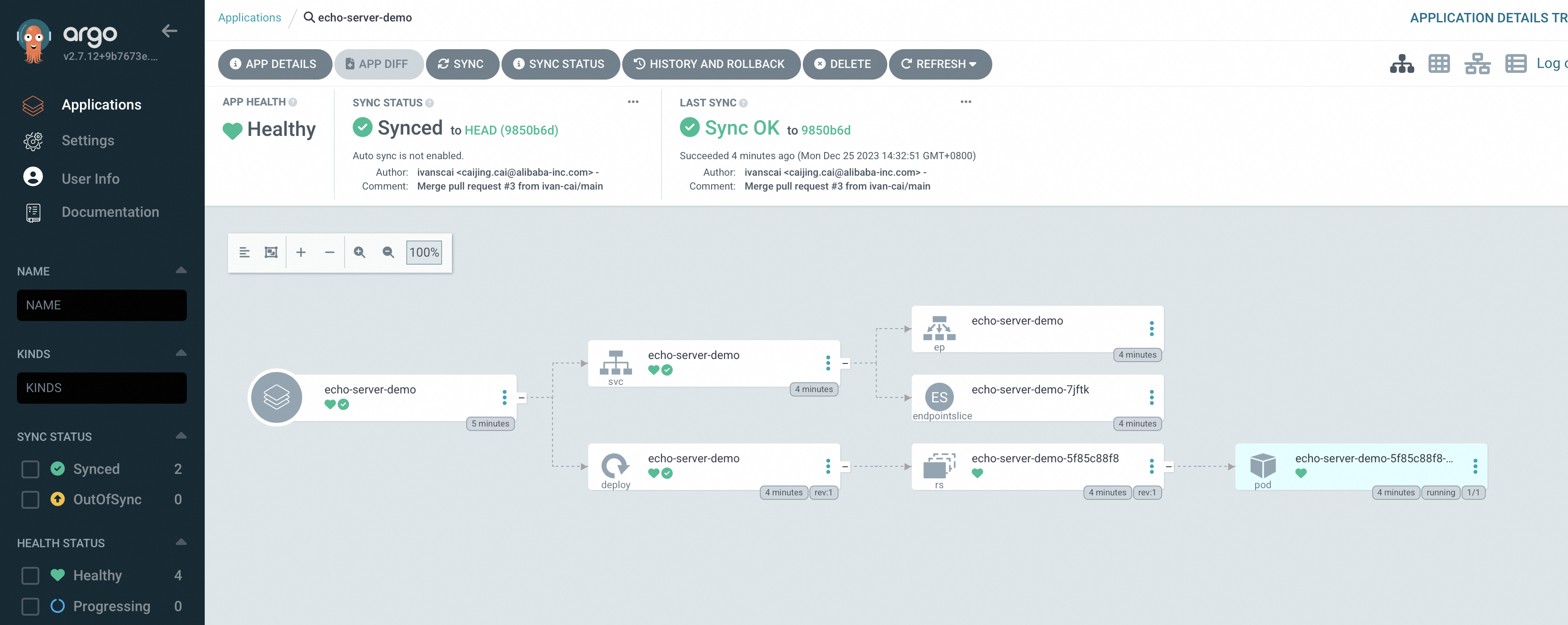
Click the name of the echo-server-demo application to view its details, including the topology and status of its related Kubernetes resources.
Deploy an application using the Argo CD CLI
Log on to and access Argo CD.
Go to ArgoCD v2.8.7 to download and install Argo CD CLI V2.8.7.
Run the following command in the ACK One fleet instance to obtain the initial password of the Argo CD system.
kubectl -n argocd get secret argocd-initial-admin-secret -o jsonpath="{.data.password}" | base64 -dRun the following command in the ACK One fleet instance to log on to Argo CD using port forwarding. The default username is
admin.export ARGOCD_OPTS='--port-forward-namespace argocd --port-forward' argocd login Username: admin Password:Expected output:
'admin:login' logged in successfully Context 'port-forward' updatedRun the following command in the ACK One fleet instance to update the password of the default
adminuser.argocd account update-password *** Enter password of currently logged in user (admin): *** Enter new password for user admin: *** Confirm new password for user admin:Expected output:
Password updated Context 'port-forward' updated
Connect to a repository.
Run the following command to add a Git repository.
argocd repo add https://github.com/AliyunContainerService/gitops-demo.git --name echo-serverExpected output:
Repository 'https://github.com/AliyunContainerService/gitops-demo.git' addedRun the following command to view the list of added Git repositories.
argocd repo listExpected output:
TYPE NAME REPO INSECURE OCI LFS CREDS STATUS MESSAGE PROJECT git https://github.com/AliyunContainerService/gitops-demo.git false false false false Successful defaultRun the following command to view the list of clusters.
argocd cluster listExpected output: The list of Argo CD clusters contains all clusters that are associated with the ACK One fleet instance.
SERVER NAME VERSION STATUS MESSAGE PROJECT https://47.97.XX.XX:6443 c83f3cbc90a****-temp02 1.22+ Successful https://kubernetes.default.svc in-cluster Unknown Cluster has no applications and is not being monitored.
Create an application.
Run the following command to create an application.
argocd app create echo-server --repo https://github.com/AliyunContainerService/gitops-demo.git --path manifests/helm --dest-namespace echo-server-cli --dest-server https://47.97.XX.XX:6443Expected output:
application 'echo-server' createdRun the following command to synchronize the application to the destination cluster.
argocd app sync echo-serverExpected output:
TIMESTAMP GROUP KIND NAMESPACE NAME STATUS HEALTH HOOK MESSAGE 2022-09-22T14:32:45+08:00 Service echo-server-cli echo-server OutOfSync Missing 2022-09-22T14:32:45+08:00 apps Deployment echo-server-cli echo-server OutOfSync Missing 2022-09-22T14:32:45+08:00 Service echo-server-cli echo-server Synced Progressing 2022-09-22T14:32:45+08:00 Service echo-server-cli echo-server Synced Progressing service/echo-server created 2022-09-22T14:32:45+08:00 apps Deployment echo-server-cli echo-server OutOfSync Missing deployment.apps/echo-server created 2022-09-22T14:32:45+08:00 apps Deployment echo-server-cli echo-server Synced Progressing deployment.apps/echo-server created Name: echo-server Project: default Server: https://47.97.XX.XX:6443 Namespace: echo-server-cli URL: https://127.0.0.1:52742/applications/echo-server Repo: https://github.com/AliyunContainerService/gitops-demo.git Target: Path: manifests/helm SyncWindow: Sync Allowed Sync Policy: <none> Sync Status: Synced to (e5c2618) Health Status: Progressing Operation: Sync Sync Revision: e5c261880a4072cdbfa5173add2be426f7f3**** Phase: Succeeded Start: 2022-09-22 14:32:44 +0800 CST Finished: 2022-09-22 14:32:45 +0800 CST Duration: 1s Message: successfully synced (all tasks run) GROUP KIND NAMESPACE NAME STATUS HEALTH HOOK MESSAGE Service echo-server-cli echo-server Synced Progressing service/echo-server created apps Deployment echo-server-cli echo-server Synced Progressing deployment.apps/echo-server createdRun the following command to view the list of applications.
argocd app listExpected output:
NAME CLUSTER NAMESPACE PROJECT STATUS HEALTH SYNCPOLICY CONDITIONS REPO PATH TARGET echo-server https://47.97.XX.XX:6443 echo-server-cli default Synced Healthy <none> <none> https://github.com/AliyunContainerService/gitops-demo.git manifests/helm
Related operations
After you deploy an application in GitOps, you can perform the following operations to improve the security and observability of the fleet and GitOps.
Configure the Argo CD ConfigMap
On the Multi-cluster GitOps page, find Argo CD ConfigMap in the GitOps collapsed section.
Click Configure next to Argo CD ConfigMap.
On the Argo CD ConfigMap Settings page, select a configuration item from the Select Configuration Item drop-down list and edit it in the Modify Configurations code editor. For more information about common configuration items and their restart policies, see Common configuration items.
Restart Argo CD components
On the Multi-cluster GitOps page, find Argo CD Component in the GitOps collapsed section.
Click Restart next to Argo CD Components.
In the dialog box that appears, select the name of the component that you want to restart from the Select Application to Restart drop-down list, for example, argocd-server, and click OK.
(Optional) Disable GitOps
If you no longer need to use GitOps, you can delete the applications in GitOps and then disable GitOps.
Before you delete an ACK One fleet instance, you must disable GitOps.
Shut down from the console
Log on to the ACK One console. In the left-side navigation pane, choose .
On the Multi-cluster GitOps page, click the
 icon next to the fleet name in the upper-left corner and select the destination fleet from the drop-down list.
icon next to the fleet name in the upper-left corner and select the destination fleet from the drop-down list.In the upper-right corner of the Multi-cluster GitOps page, click Disable GitOps. In the message that appears, click OK.
Shutdown using the Cloud Assistant CLI
Make sure that you are using the latest version of Cloud Assistant CLI. Then, run the following command to disable GitOps.
aliyun adcp UpdateHubClusterFeature --ClusterId <your_clusterid> --ArgoCDEnabled false