You can test the network connectivity between an API Gateway instance and an instance in a VPC to which you have granted access permissions. This helps you identify network connectivity issues that may cause API call failures during API debugging. This topic describes the VPC access authorization connectivity test feature and provides a guide to troubleshoot connectivity test failures.
VPC authorization
A VPC access authorization creates a record that allows API Gateway to access a business service that you deploy in your VPC. When you create a VPC access authorization, you must provide the VPC ID, the instance ID of the CLB or ECS instance that provides the service, and the service port number. This information uniquely identifies a business service and authorizes API Gateway to access it. For more information, see Use a resource in a VPC as the backend service of an API.
Perform a connectivity test
Log on to the API Gateway console. In the navigation pane on the left, choose , and create a VPC access authorization.
Click Test Connectivity and select the destination API Gateway instance.
ImportantMake sure that no access control policy is configured for the selected instance. Otherwise, the connectivity test may fail.
Click Test. A network probe is initiated from the selected API Gateway instance to the business service specified in your VPC access authorization. After the test is complete, the result is displayed on the page.
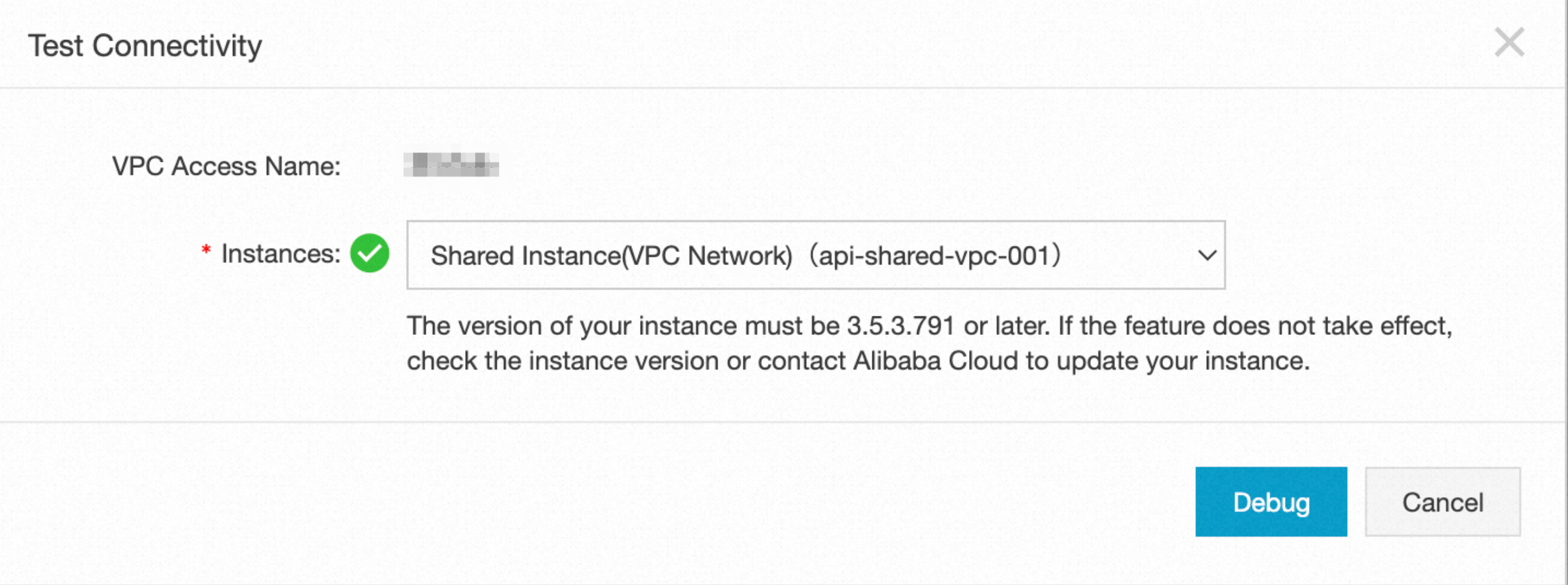
Test passed
If the network between the API Gateway instance and the service in your VPC access authorization is connected, a green check mark appears before the instance drop-down list. This indicates that the connectivity test is successful.
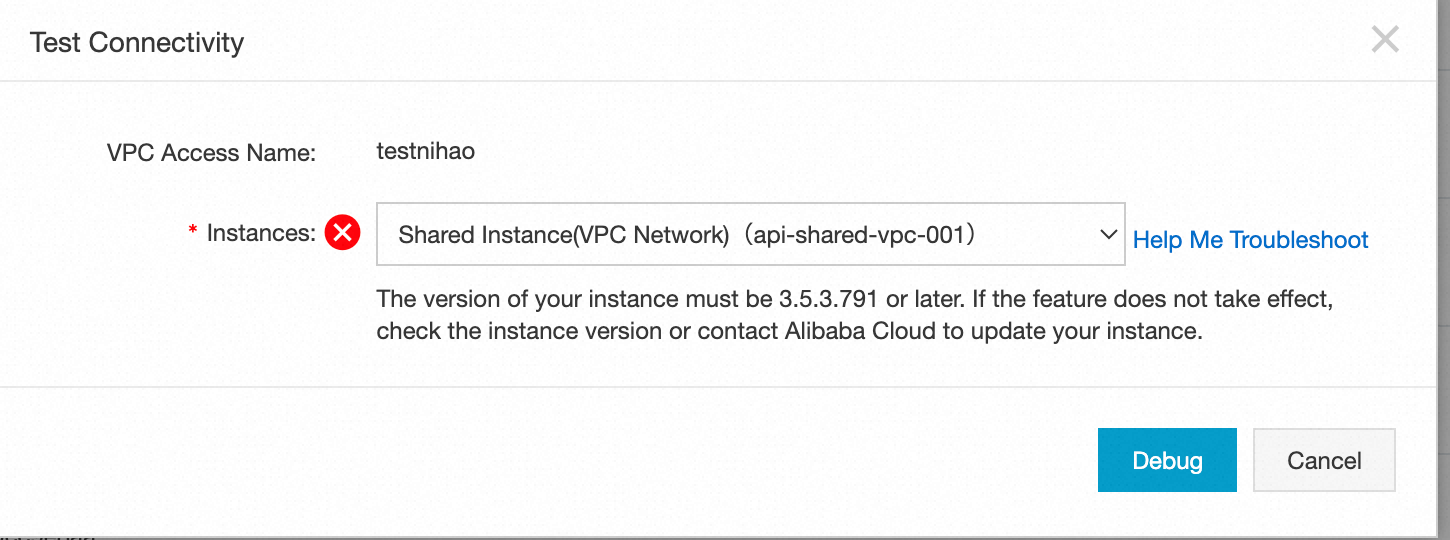
Test failed
If the connectivity test fails, a prompt appears. This indicates that the network between the API Gateway instance and the service in your VPC access authorization is disconnected. If the test fails, you can click Troubleshooting Guide and follow the prompts to troubleshoot the issue.
Troubleshooting guide
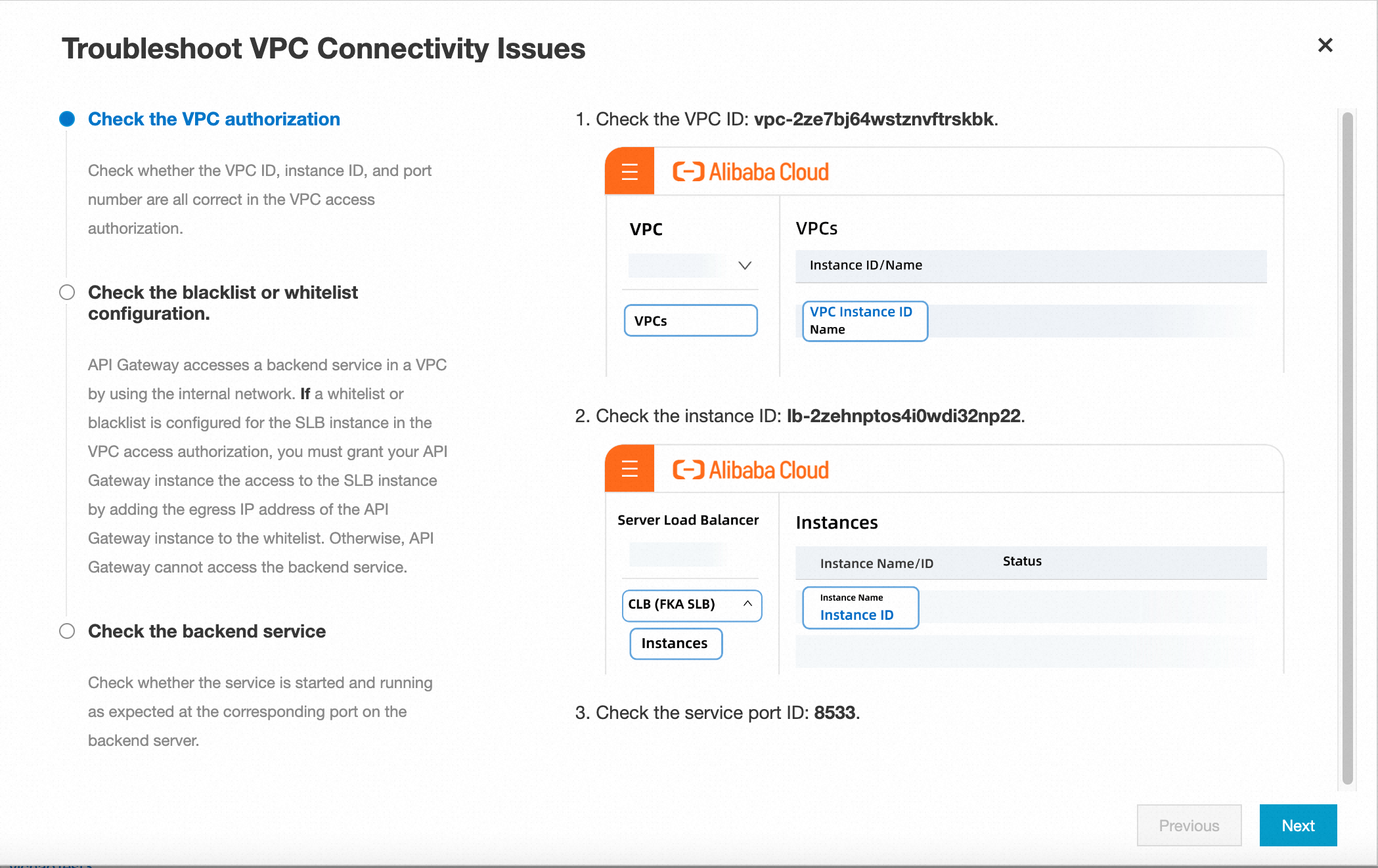
If the network is disconnected, you can click Troubleshooting Guide to open a pop-up window. The window provides a series of steps to guide you through the troubleshooting process. The pop-up window displays troubleshooting instructions for a CLB or ECS instance, depending on the instance type specified in your VPC access authorization. Follow the prompts to troubleshoot the issue.
The troubleshooting procedure consists of the following three steps:
Check whether the VPC authorization information is correct.
When you create a VPC access authorization, you must specify the VPC ID, instance ID, and service port. In this step, you are prompted to navigate to the console of the corresponding cloud product to verify that the information you entered is correct.
Check the security group of the ECS instance (or the blacklists and whitelists of the CLB instance).
If the instance in your VPC access authorization is an ECS instance with a configured security group, you must navigate to the ECS console. Then, add the egress IP address of the API Gateway instance to the inbound policy of the security group for the ECS instance, as prompted.
If the instance in your VPC access authorization is a CLB instance with a configured whitelist-based access control policy, you must add the egress IP address of the API Gateway instance to the address entries of the corresponding access control policy group.
Check the startup status of the backend service.
In this step, you must check the running status and health status of the backend service. If the instance specified in the VPC access authorization is an ECS instance, check the health status of the ECS instance. If the instance is a CLB instance, check that the running status and health check status of its configured listener are Normal. To verify the port, you can log on to any server in your VPC and run the curl command to check whether the corresponding port on the configured ECS or CLB instance is in a listening state.