Cloud-native API Gateway is integrated with Web Application Firewall 3.0. You can use WAF 3.0 for Cloud-native API Gateway instances or routes to provide end-to-end security protection for your websites or applications.
Background information
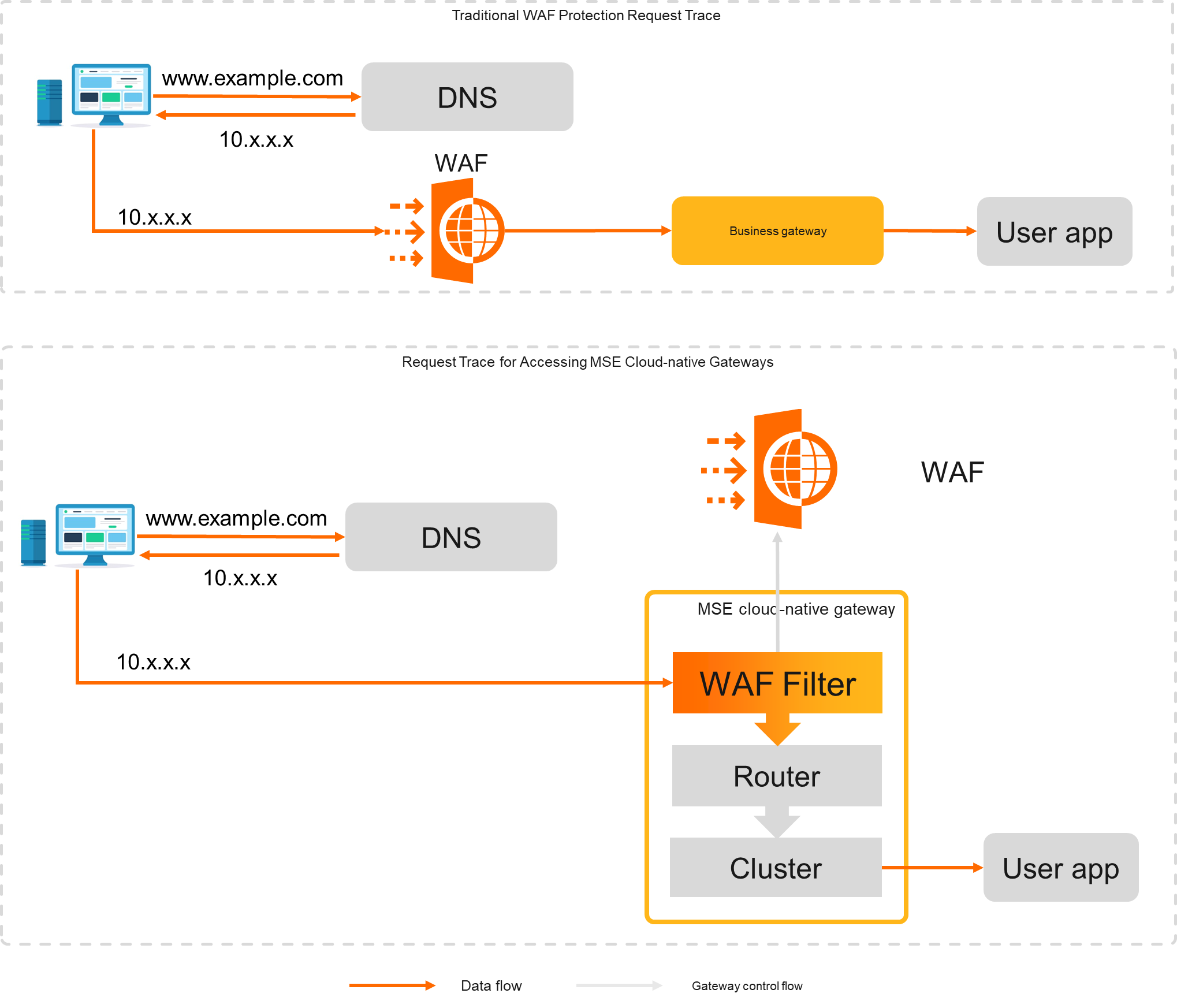
WAF can efficiently identify the features of malicious traffic and distribute only business traffic to backend servers after traffic scrubbing and filtering. This prevents server performance issues caused by intrusions and ensures the security of websites and data. Unlike traditional web application firewalls, user traffic directly reaches your Cloud-native API Gateway instance without the need to pass through a web application firewall. This improves the overall system performance without compromising security. The following figure shows the difference.
Billing
Cloud-native API Gateway does not charge fees for using WAF 3.0. However, WAF 3.0 charges you fees based on your actual usage.
How to enable WAF 3.0
Cloud-native API Gateway console: We recommend that you use this method. For more information, see Enable WAF 3.0 for an instance and Enable WAF 3.0 for a route.
Enable WAF 3.0 for an instance
This operation may cause the instance to restart.
Log on to the Cloud-native API Gateway console. In the left-side navigation pane, click Instance. In the top navigation bar, select a region.
NoteThe WAF 3.0 integration feature is not available in China East 2 Finance.
On the Instance page, click the ID of the Cloud-native API Gateway instance that you want to manage.
In the Enable instance-level WAF protection dialog box, click Continue to enable instance-level WAF protection (recommended).
Enable WAF 3.0 for a route
This operation may cause the instance to restart.
Log on to the Cloud-native API Gateway console.
In the left-side navigation pane, click API. In the top navigation bar, select a region.
Click the HTTP or WebSocket API that you created. On the API details page, click the name of the route that you want to manage. On the Configure Policy tab, click WAF and click Enable Rout-level WAF Protection (Recommended) on the right side.
In the Enable Route-level WAF Protection dialog box, click OK.
What to do next
After WAF 3.0 is enabled, your website traffic is inspected by the built-in WAF protection feature. WAF automatically enables rule-based protection and HTTP flood protection. Rule-based protection can protect your website against common web attacks, such as SQL injection, Cross-Site Scripting (XSS) attacks, and malicious webshell uploads. HTTP flood protection can protect your website against HTTP floods. If you require additional protection, you can manually activate other modules and configure protection rules. For more information, see Overview.
FAQ
Does Cloud-native API Gateway support WAF 2.0?
Yes. To integrate Cloud-native API Gateway with WAF 2.0, you must add the IP address of the Server Load Balancer (SLB) instance that is associated with your Cloud-native API Gateway instance as a back-to-origin IP address of WAF. For more information, see Tutorial.