Alibaba Cloud Content Delivery Network (CDN) では、証明書と秘密鍵を PEM 形式でのみアップロードできます。また、異なる認証局 (CA) によって発行された証明書には、それぞれ異なる要件があります。
ルート CA によって発行された証明書
ルート証明書はルート CA によって発行され、Apache、IIS、NGINX、Tomcat などの Web サーバーで使用できます。CDN で使用される SSL 証明書は、NGINX と互換性があります。各証明書には、.crt および .key の名前拡張子を持つ 2 つのファイルが含まれています。
NGINX フォルダーを開き、テキストエディターを使用して .crt ファイルを開きます。その後、証明書の内容を表示できます。次の図は例を示しています。
図 1. PEM 形式の証明書 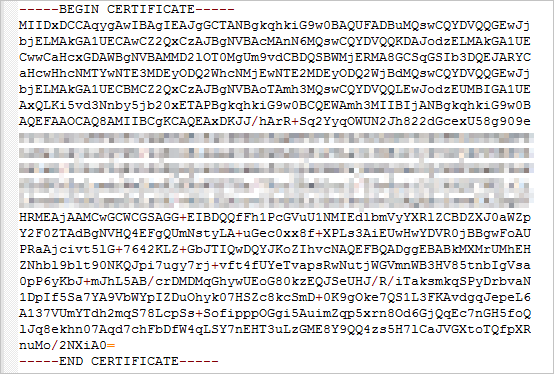
PEM 形式の証明書
証明書は "-----BEGIN CERTIFICATE-----" で始まり、"-----END CERTIFICATE-----" で終わる必要があります。
各行 (最終行を除く) には 64 文字が含まれている必要があります。最終行には、64 文字以下の文字を含めることができます。
証明書のアップロード要件
"-----BEGIN CERTIFICATE-----" で始まり、"-----END CERTIFICATE-----" で終わる証明書のすべてのコンテンツをアップロードする必要があります。
各行 (最終行を除く) には 64 文字が含まれている必要があります。最終行には、64 文字以下の文字を含めることができます。
中間 CA によって発行された証明書
HTTPS を構成する場合は、証明書をアップロードする前に、中間証明書とサーバー証明書を組み合わせて完全な証明書にする必要があります。次の図は、完全な証明書の例を示しています。
図 2. PEM 形式の完全な証明書
証明書チェーンの形式
中間 CA によって発行された証明書は、次の形式です。
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
結合ルール
テキストエディターを使用して、すべての *.PEM 証明書ファイルを開きます。証明書を組み合わせるときは、最初の証明書はサーバー証明書である必要があり、中間証明書はサーバー証明書の後に続きます。証明書間にスペース文字を追加しないでください。
RSA 秘密鍵の形式
秘密鍵ファイルの拡張子は、.pem または .key です。テキストエディターを使用して、秘密鍵ファイルを開きます。次の図は、秘密鍵ファイルの例を示しています。
図 3. RSA 秘密鍵の形式
PEM 形式の秘密鍵
秘密鍵は "-----BEGIN RSA PRIVATE KEY-----" で始まり、"-----END RSA PRIVATE KEY-----" で終わる必要があります。
各行 (最終行を除く) には 64 文字が含まれている必要があります。最終行には、64 文字以下の文字を含めることができます。
秘密鍵のアップロード要件
RSA 秘密鍵をアップロードする前に、オンプレミス マシンで openssl genrsa -out privateKey.pem 2048 コマンドを実行して、秘密鍵を生成します。privateKey.pem ファイルは秘密鍵ファイルです。
秘密鍵は "-----BEGIN RSA PRIVATE KEY-----" で始まり、"-----END RSA PRIVATE KEY-----" で終わる必要があります。
各行 (最終行を除く) には 64 文字が含まれている必要があります。最終行には、64 文字以下の文字を含めることができます。
"-----BEGIN PRIVATE KEY-----" で始まり、"-----END PRIVATE KEY-----" で終わる秘密鍵を生成する場合は、OpenSSL で次のコマンドを実行して形式を変換します。次に、new_server_key.pem ファイルの内容と証明書をアップロードします。
openssl rsa -in old_server_key.pem -out new_server_key.pem証明書形式の変換
HTTPS 機能は、PEM 形式の証明書のみをサポートしています。証明書が PEM 形式でない場合は、証明書を PEM 形式に変換する必要があります。OpenSSL を使用して証明書形式を変換することをお勧めします。次のセクションでは、証明書を PEM 形式に変換する方法について説明します。
CRT ファイルは、PEM 形式または Distinguished Encoding Rules (DER) 形式の場合があります。証明書を変換する必要があるかどうかを確認してください。
PEM はテキスト形式です。"-----BEGIN ***-----" で始まり、"-----END ***-----" で終わります。これらの行の間のコンテンツは Base64 でエンコードされています。PEM 形式の秘密鍵ファイルの拡張子は
.keyです。
証明書形式を DER から PEM に変換する
ほとんどの場合、DER 形式は Java に使用されます。
証明書形式を変換します。
openssl x509 -inform der -in certificate.cer -out certificate.pem秘密鍵の形式を変換します。
openssl rsa -inform DER -outform pem -in privatekey.der -out privatekey.pem
証明書形式を P7B から PEM に変換する
ほとんどの場合、P7B 形式は Windows Server および Tomcat に使用されます。
証明書形式を変換します。
openssl pkcs7 -print_certs -in incertificat.p7b -out outcertificate.ceroutcertificate.cerファイルを開きます。次に、"-----BEGIN CERTIFICATE-----" で始まり、"-----END CERTIFICATE-----" で終わる部分をコピーしてアップロードします。秘密鍵の形式を変換します。
P7B 形式の証明書には、秘密鍵は含まれていません。CDN コンソールで SSL 証明書を構成する場合は、証明書情報を指定します。秘密鍵情報を指定する必要はありません。
証明書形式を PFX から PEM に変換する
ほとんどの場合、PFX 形式は Windows Server に使用されます。
証明書形式を変換します。
openssl pkcs12 -in certname.pfx -nokeys -out cert.pem秘密鍵の形式を変換します。
openssl pkcs12 -in certname.pfx -nocerts -out key.pem -nodes