Ransomware is a common type of computer virus. After an Elastic Compute Service (ECS) instance is infected with ransomware, the business data on the instance is encrypted and used for ransom. This can lead to serious business risks, such as service interruptions, data leaks, and data loss. This topic describes how to improve the anti-ransomware capabilities of an ECS instance.
Background information
As computer and cloud computing technologies develop, various types of computer viruses emerge, including ransomware, which is a particularly common type. Alibaba Cloud leverages years of experience in cloud security protection and advanced security attack-and-defense technologies to provide users with comprehensive security solutions. For more information about anti-ransomware, see Overview of anti-ransomware.
Problem description
When your ECS instance is infected with ransomware, the system files are encrypted, and a ransom note or message appears in your working directory. For example, if a Windows ECS instance is infected with ransomware, the following ransom note appears in your working directory.
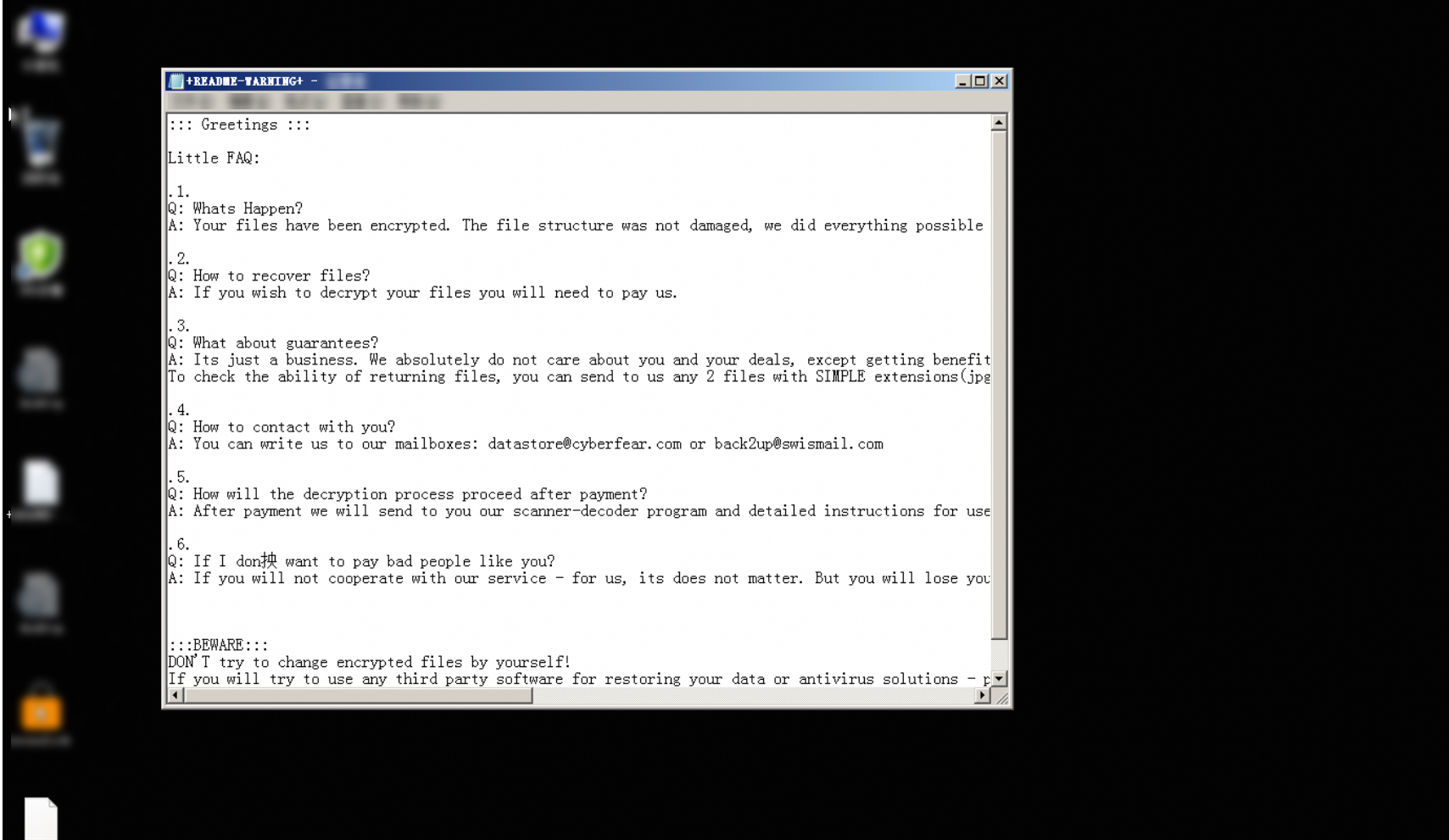
Solution overview
Computer virus prevention measures can reduce the risk of virus infection, but the prevention measures cannot completely eliminate virus infection. Data backup provides the final protection against ransomware. However, when you restore data for a disk from a backup or snapshot, data from the point in time when the backup or snapshot is created to the point in time when the disk is rolled back is lost. You must properly design a data backup policy based on your business scenario to effectively protect important data.
The following solutions provide common protection ideas for ransomware:
Solution 1: Use Security Center to improve the anti-ransomware capabilities of an ECS instance
Solution 2: Use an automatic snapshot policy to create snapshots for an ECS instance
You can use a single solution or a combination of the preceding solutions based on your business requirements. For example, if you have high requirements for business continuity, you can use all the preceding solutions at the same time. Take note that you are charged for backups or snapshots.
Solution 1: Use Security Center to improve the anti-ransomware capabilities of an ECS instance
Workflow

Procedure
Enable the anti-ransomware feature and purchase the anti-ransomware capacity.
To use the anti-ransomware feature provided by Security Center, you must enable the feature and purchase the anti-ransomware capacity. For more information, see Enable anti-ransomware.
NoteYou can purchase anti-ransomware services based on your business scenario and requirements.
Create an anti-ransomware policy.
After you enable the anti-ransomware feature, you must create an anti-ransomware policy.
(Optional) Restore data from a valid backup in Security Center.
Create snapshots for the system disk and data disks of the instance that is infected with ransomware. For information about how to create a snapshot, see Create a snapshot manually.
Use a backup in Security Center to restore your business. To restore your business, perform the following steps.
Solution 2: Use an automatic snapshot policy to create snapshots for an ECS instance
Workflow

Procedure
Snapshots are backups that can be used to restore data after the instance based on which the snapshots are created is infected with ransomware. Take note that this solution only provides post-event restoration capabilities and cannot replace active protection measures.
Create an automatic snapshot policy for the disks attached to the instance. For more information, see Create an automatic snapshot policy.
(Optional) Restore data from valid snapshots that were created before the instance is infected with ransomware.
Create snapshots for the system disk and data disks of the instance that is infected with ransomware. For information about how to create a snapshot, see Create a snapshot manually.
ImportantThe rollback operation is irreversible. After you roll back a disk, data that you added, removed, or modified from the point in time when the snapshot is created to the point in time when the disk is rolled back is lost. To prevent data loss caused by accidental operations, we recommend that you create snapshots for the disks attached to the instance to back up data before you roll back the disks.
Re-initialize the system disk of the instance. For more information, see Re-initialize a system disk (reset the operating system).
Use valid snapshots that were created before the instance is infected with ransomware to restore the data of the system disk and data disks. For more information, see Roll back a disk by using a snapshot.
Solution 3: Use security policies such as security groups and firewalls to improve instance protection
Workflow

Procedure
You can use security policies, such as security groups and firewalls, to improve protection capabilities against ransomware. This requires that you have technical expertise on network security.
Learn about the best practices for security groups and firewall policies and configure security settings. For more information, see Best practices for security groups (inbound rules) and Configure firewall rules for a Windows ECS instance.
(Optional) Contact a third-party organization to decrypt and restore ransomware-corrupted data.
Create snapshots for the system disk and data disks of the instance that is infected with ransomware. For information about how to create a snapshot, see Create a snapshot manually.
Re-initialize the system disk of the instance. For more information, see Re-initialize a system disk (reset the operating system).
If you do not back up important data or create snapshots before you re-initialize the system disk, you can contact a third-party organization to decrypt and restore the ransomware-corrupted data after you re-initialize the system disk of the instance.
WarningThe data decryption capability provided by a third-party organization after a ransomware attack is independent of Alibaba Cloud. Alibaba Cloud is not responsible for the extent of data restoration and possible data corruption.
References
Refer to the following topics if needed: