Alibaba Cloud offers several connection methods. Choose the one that best suits your needs based on the Elastic Compute Service (ECS) instance's operating system, security requirements, convenience, and network environment.
Choose a connection tool
Connection tool | Supported OS | Local installation required | Public network access required | Password-free login supported | Alibaba Cloud login required |
Workbench (browser) | Windows, Linux | No | No | Yes | Yes |
Session Manager (browser) | Windows, Linux | No | No | Yes | Yes |
VNC (browser) | Windows, Linux | No | No | No | Yes |
Alibaba Cloud Client | Windows, Linux | Yes | No | Yes | Yes |
SSH client (third-party) | Linux | Yes | Yes | No | No |
RDP client (third-party) | Windows | Yes | Yes | No | No |
Connection tools and guides
WorkbenchWorkbench is a browser-based remote connection tool provided by Alibaba Cloud that requires no local installation. It supports features such as file transfer and multi-terminal. References | Alibaba Cloud ClientAlibaba Cloud Client is official software for managing your resources. After installing the client, you can connect to your ECS instances. References |
Session ManagerSession Manager is a high-security connection feature provided by Cloud Assistant. It eliminates the need for a public IP address, which protects your instance from external attacks. It also provides a full audit trail of all operations. References | SSH client (third-party)To use a third-party SSH client, your instance must have a public IP address or an Elastic IP Address (EIP). Common SSH clients include OpenSSH, PuTTY, and XShell. Reference Use an SSH key pair to connect to a Linux instance from an OpenSSH or Xshell client |
VNCVNC lets you view the real-time interface of the operating system on an instance. You can view the system interface even during instance startup or shutdown. Because VNC operates independently of Security Group rules and software on the instance, you can use it to troubleshoot connection issues when other methods fail. Reference | RDP client (third-party)To use a third-party RDP client to connect to a Windows instance, assign a public IP address or an EIP to the instance. Common RDP clients include Microsoft Remote Desktop, Windows Remote Desktop, and Windows App. References |
FAQ
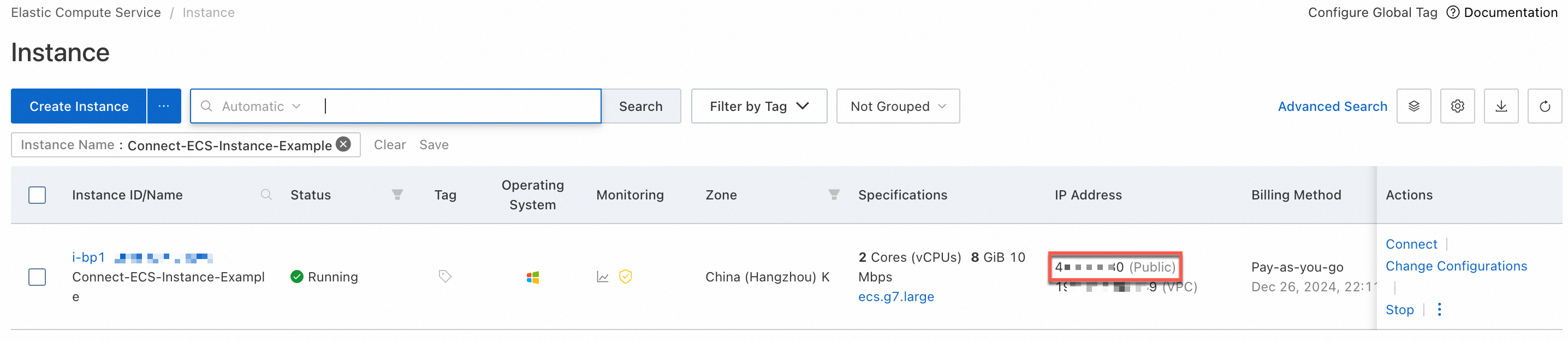
How do I check if an instance is assigned a public IP address?
Check the Instance page to see if your instance has a public IP address. If no public IP address is assigned, enable public bandwidth.
How do I check the operating system of an ECS instance?
You can view the instance's operating system information on the Instance page. Most non-Windows operating systems are Linux-based. The following image shows an ECS instance running Windows.
To change the operating system, see Replace the operating system (system disk).