App防护专门针对原生App端,提供可信通信、防机器脚本滥刷等安全防护,可以有效识别代理、模拟器、非法签名的请求。本文介绍了在应用端集成App防护SDK后,如何在Web应用防火墙控制台设置App防护的防护路径和版本防护功能,以及如何开启App防护。
前提条件
已开通Web应用防火墙实例,且实例开启了App防护模块。
已在App中集成Web应用防火墙的App防护SDK。更多信息,请参见概述。
操作步骤
登录Web应用防火墙控制台。
在顶部菜单栏,选择Web应用防火墙实例的资源组和地域(中国内地、非中国内地)。
在左侧导航栏,选择。
在网站防护页面上方,切换到要设置的域名。
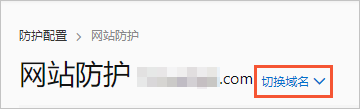
单击Bot管理页签,定位到App防护,单击前去配置。
说明App防护开启后,所有业务请求默认都会经过App防护规则的检测。您可以通过设置Bot管理白名单,让满足条件的请求忽略App防护规则的检测。更多信息,请参见设置Bot管理白名单。
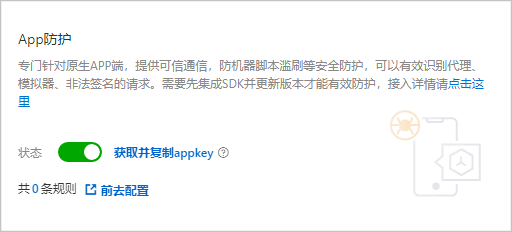
设置路径防护规则。
在App防护页面,定位到路径防护区域,单击新建规则。
在新建规则对话框,完成以下规则配置。
 说明
说明建议您在测试阶段设置全路径防护(Path设置为
/,匹配方式选择前缀匹配),并将处置动作设置为观察(如果是测试域名,可以设置为阻断)。这样可以在不影响线上业务的前提下进行调试。参数
说明
规则名称
为规则命名。
防护路径配置
设置要防护的路径信息,包含以下参数:
Path:要防护的路径地址。使用正斜杠(/)表示全路径。
说明POST请求的body长度超过8 KB的情况下,可能会造成验签失败。如果该类型接口没有防护必要(如上传大图片等),建议不要经过SDK防护;如确实有防护必要,请使用自定义加签字段。
匹配方式 :支持前缀匹配、精确匹配和正则匹配。
前缀匹配会匹配指定路径下的所有接口,精确匹配只匹配指定路径,正则匹配支持以正则表达式的方式描述指定路径。
参数包含:要防护的路径下包含固定参数时,指定要匹配的参数内容,更准确地定位接口。参数内容指请求地址中问号后面的内容。
示例:假设要防护的URL包括
域名/?action=login&name=test。您可以将Path设置为“/”,匹配方式设置为“前缀匹配”,并在参数包含中填写“name”、“login”、“name=test”、“action=login”。防护策略
选择要应用的防护策略:
非法签名:默认选中(不支持取消),验证对指定路径的请求的签名是否正确。签名不正确则命中规则。
模拟器:选中后,检测用户是否使用模拟器对指定路径发起请求。使用模拟器则命中规则。
代理:选中后,检测用户是否使用代理工具对指定路径发起请求。使用代理工具则命中规则。
处置动作
选择对命中防护策略的用户请求执行的操作:
观察: 只记录日志,不阻断请求。
阻断: 阻断请求,返回405状态码。
重要未集成SDK或未调试完成前,请不要为生产环境中的域名开启阻断模式,否则可能会因为SDK没有正确集成导致合法请求被拦截。在测试接入阶段,可以开启观察模式,通过日志调试SDK集成。
自定义加签字段
启用自定义加签字段后,系统将根据所设置的需要加签的请求字段和对应的字段值进行加签验证,判断是否命中该防护策略。
系统默认情况对请求的body加签,如果body长度超过8 KB则可能导致验签失败。这种情况下,您可以启用自定义加签字段,使用您指定的请求字段来取代系统默认的加签字段。
启用自定义加签字段后,您可以选择请求Header、参数或Cookie类型,然后填写需要加签的字段即可。例如,您可以选择cookie,填写“DG_ZUID”,请求Cookie中的DG_ZUID字段将取代系统默认的body字段作为加签字段。
单击确定。
开启版本防护。
通过配置版本防护可以拦截来自非官方App的请求。如果您需要验证App合法性,可通过配置该策略实现。
说明如果不需要进行App合法性验证,则可不配置版本防护策略。
在App防护页面,定位到版本防护,开启仅允许指定版本通过开关。
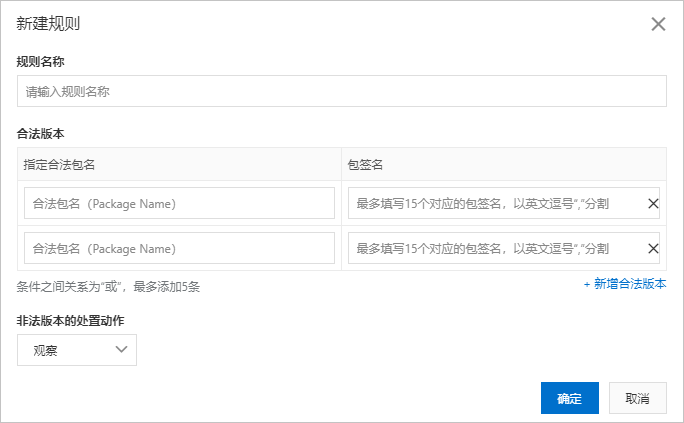
在新建规则对话框,完成以下规则配置。
参数
说明
规则名称
为规则命名。
合法版本
设置合法版本信息:
指定合法包名:指定合法的App包名称。例如,com.aliyundemo.example。
包签名:请联系阿里云相关安全技术人员获取。如果无需验证对应的App包签名,则包签名项为空即可,将只验证所设定的合法App包名称。
重要包签名不是App证书签名。
单击新增合法版本可以添加最多5条版本记录,包名称不允许重复。iOS和Android包都支持,合法的记录都可以填写进去以匹配多个包名。
非法版本的处置动作
观察:只记录日志,不阻断请求。
阻断:阻断请求,返回405状态码。
单击确定。
开启App防护。回到App防护区域,开启状态开关。
说明建议您通过调试确定已在App中正确集成SDK并发布新版App后,再开启App防护,使防护配置生效。