Mellanox Technologies (NASDAQ: MLNX) is a leading supplier of end-to-end Ethernet and InfiniBand intelligent interconnect solutions and services for servers, storage, and hyper-converged infrastructure. Founded in 1999, Mellanox Technologies is headquartered in Sunnyvale, California and Yokneam, Israel. Mellanox offers a choice of high-performance solutions for a wide range of markets including high performance computing, enterprise data centers, Web 2.0, cloud, storage, network security, telecom and financial services. [1]
This article will focus on a security feature provided by Mellanox's network interface card (NIC): the secure firmware updates. This security feature is becoming a basic requirement for a hardware device to be a part of Alibaba Cloud. Secure firmware updates feature provide devices with the ability to verify digital signatures of new firmware binaries, in order to ensure that only officially approved versions are installed on the devices. With this feature, the Mellanox NIC and SmartNIC can become the more trusted devices on Alibaba Cloud.
Note: the content of this chapter referrers to Mellanox documents.
The firmware of devices on which the secure firmware updates functionality is enabled, restricts access to registers that can be used to modify the firmware binary image on the flash, as well as commands that can jeopardize security in general. The differences between secure and regular devices are mainly related to maintenance and low-level troubleshooting. In all other aspects, devices with secure firmware are similar to regular devices.
Secure firmware binary files are digitally signed by Mellanox according to the PKCS RSASSA-PKCS1-v1_5 standard. This FIPS approved signature algorithm, utilizes SHA256 digest and 2048 bits RSA cryptography. The running firmware uses its embedded public keys to authenticate signatures of new updates, while the corresponding private keys are kept within and protected by Mellanox dedicated sign servers.
Here are some advantages of a device running secure firmware over the one that does not:
Note: the content of this chapter referrers to Mellanox documents.
The Mellanox Firmware Tools (MFT) package is a set of firmware management and debug tools for Mellanox devices. MFT can be used for generating a standard or customized Mellanox firmware image, querying for firmware information, and burning a firmware image to a single Mellanox device.
In contrast to the old firmware update procedure, where the update application is responsible for the entire update flow, in secure FW, the update application operates a state machine in the firmware that performs the update procedure. This includes checking the new binary applicability, integrity, and burning the image in the right flash location.
Additionally, the firmware state machine is also responsible to verify the image signature, and check that the new FW version is not included in the FORBIDDEN_VERSIONS blacklist. The firmware rejects binaries that do not match the verification criteria. The state- machine utilize the same 'fail safe' upgrade procedures, so events like power failure during update should not leave the device in an unstable state.
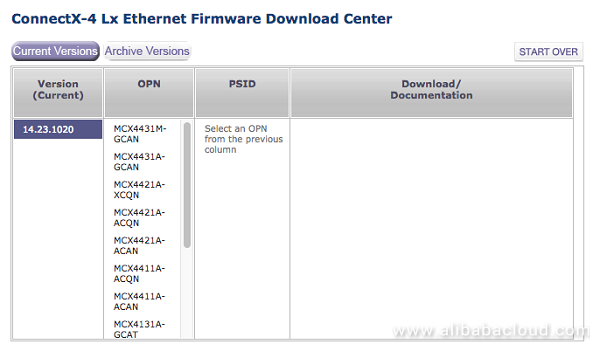
In the example below, we used Mellanox Technologies MT27710 Family [ConnectX-4 Lx]. The operation system is Ubuntu 16.04.2.
The MFT installation package can be downloaded at: http://www.mellanox.com/page/management_tools
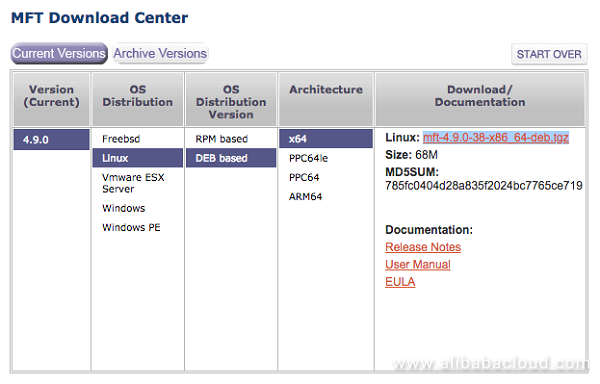
The firmware image can be downloaded at: http://www.mellanox.com/page/firmware_table_ConnectX4LxEN
./install.sh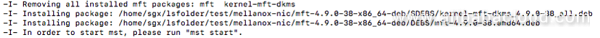
mst start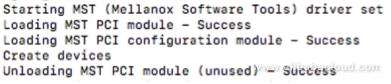
mst status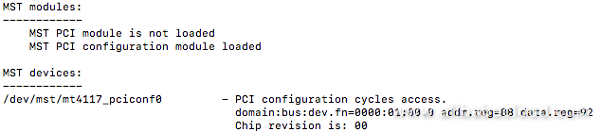
flint -d /dev/mst/mt4117_pciconf0 q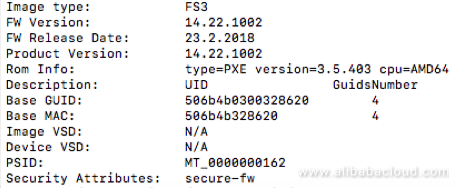
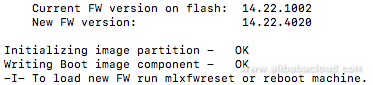
flint -d /dev/mst/mt4117_pciconf0 q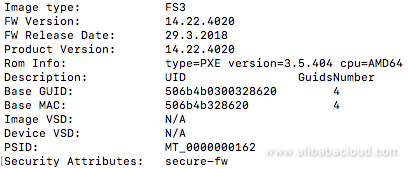
flint -d /dev/mst/mt4117_pciconf0 -i fw-ConnectX4Lx-rel-14_22_4020-MCX4121A-ACS_Ax-FlexBoot-3.5.404.bin b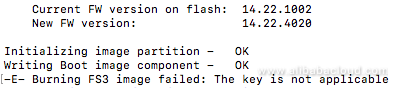
flint -d /dev/mst/mt4117_pciconf0 q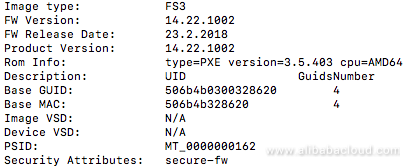
Secure firmware updates feature is a basic requirement for a trusted hardware device to be used on Alibaba Cloud. Mellanox's NICs offer this important security feature now.
Alibaba Cloud Community - July 27, 2022
Alibaba Clouder - July 5, 2018
Alibaba Cloud Community - January 6, 2022
Dikky Ryan Pratama - May 17, 2023
Alibaba Clouder - August 13, 2019
Alibaba Container Service - February 13, 2019
 Networking Overview
Networking Overview
Connect your business globally with our stable network anytime anywhere.
Learn More Edge Network Acceleration
Edge Network Acceleration
Establish high-speed dedicated networks for enterprises quickly
Learn More Quick Starts
Quick Starts
Deploy custom Alibaba Cloud solutions for business-critical scenarios with Quick Start templates.
Learn More Accelerated Global Networking Solution for Distance Learning
Accelerated Global Networking Solution for Distance Learning
Alibaba Cloud offers an accelerated global networking solution that makes distance learning just the same as in-class teaching.
Learn More