The Istio community website lists a Bookinfo example for beginners to quickly learn about some concepts and capabilities of the service mesh technology. This article demonstrates the quick-start tutorial provided by Alibaba Cloud Service Mesh (ASM) concerning how to deploy the Bookinfo example. This article is the second edition in the ASM Public Preview Series, a collection of articles that describes key capabilities of Alibaba Cloud Service Mesh (ASM). Find below the links to other articles in this series:

The quick-start tutorial includes the following steps:
To use ASM, it is imperative to create an ASM instance.
Activate the following services:
When you create an ASM instance, ASM may perform the following operations based on the configuration:
1) Log on to the ASM console.
2) In the left-side navigation pane, click ASM Instance and then Create ASM Instance on the right.
3) On the Create ASM Instance page, enter the ASM instance name and select a region, VPC, and VSwitch.
Note: You can select the required VPC and VSwitch from the existing VPC list and VSwitch list. If the required VPC or VSwitch is not listed in the existing VPC list or VSwitch list respectively, click Create VPC to create a VPC instance or click Create VSwitch to create a VSwitch. For more information, see Create a VPC and Create a VSwitch.
4) Determine whether to select Expose API Server with EIP.
If an ASM instance runs on Kubernetes, you may define various ASM resources, such as virtual services, target rules, and Istio gateways through API Server.
i) If Expose API Server with EIP is selected, an EIP will be created and mounted to the VPC SLB instance. Port 6443 of API Server will be exposed. Use the kubeconfig file to connect to and operate clusters and define ASM resources through the internet.
ii) If Expose API Server with EIP is not selected, no EIP will be created. In this case, you must use the kubeconfig file to connect to and operate clusters and define ASM resources in the VPC instance.
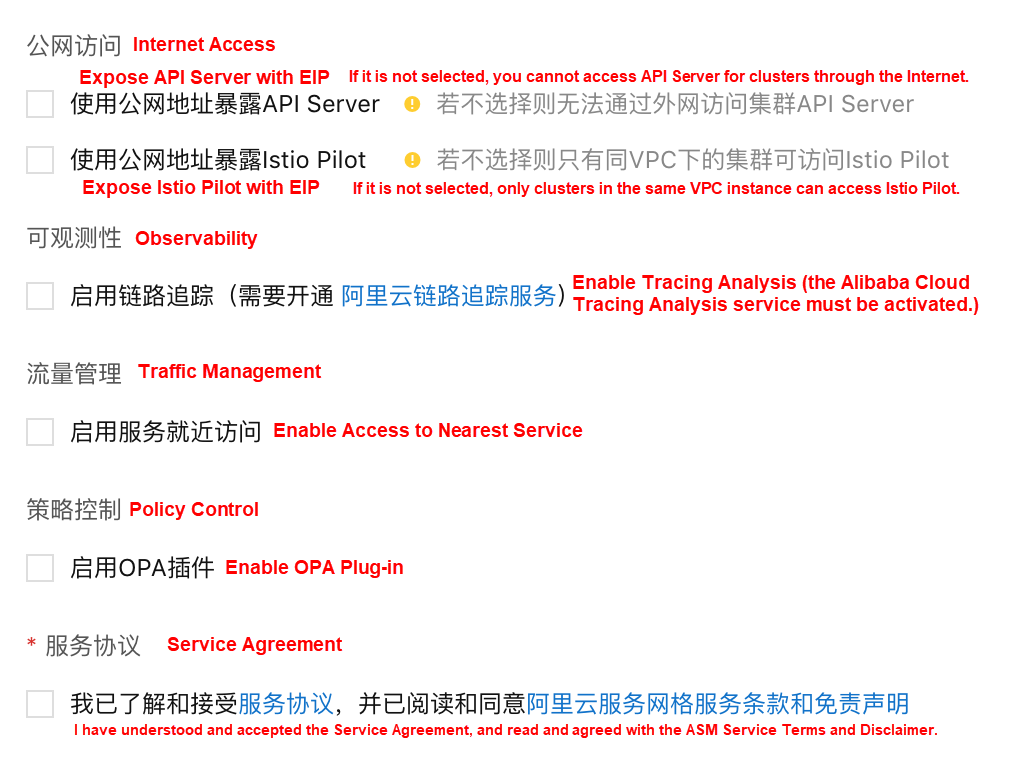
5) Determine whether to select Expose Istio Pilot with EIP.
i) If Expose Istio Pilot with EIP is selected, an EIP will be created and mounted to the VPC SLB instance. Port 15011 of Istio Pilot will be exposed. Envoy proxies deployed in data-plane clusters may use this public IP address to connect to Istio Pilot.
ii) If Expose Istio Pilot with EIP is not selected, no EIP will be created. In this case, only clusters interconnected with the VPC instance can be added to the data plane, including clusters in the same VPC and cross-VPC clusters that are connected through Cloud Enterprise Network.
Note: Expose Istio Pilot with EIP is not selected by default, and the data and control planes are preferentially connected through the VPC instance.
6) Observability: Determine whether to select Enable Tracing Analysis.
ASM integrates with the Alibaba Cloud Tracing Analysis service, which provides distributed application developers with tools, such as trace recovery, request count, link topology, and application dependency analysis. It helps developers quickly analyze and diagnose performance bottlenecks in the distributed application architecture and improve the efficiency of development and diagnosis.
Note: To select this option, you need to first log on to the Tracing Analysis console and enable the Tracing Analysis service.
7) Traffic Management: Determine whether to select Enable Access to Nearest Service.
ASM provides global load balancing capabilities to application services through the Envoy proxy. You can deploy application services in cross-region ACK clusters. ASM provides the running status, routing, and backend information of these application services to the Envoy proxy. The Envoy proxy then routes traffic to the application instance whose services run in multiple regions in the most optimal way. ASM will prioritize the workload instances of the target service based on the location of the Envoy proxy that sends requests. After this option is selected, requests are preferentially sent to service instances located in the same region when all instances are normal to ensure access to the nearest service.
8) Policy Control: Determine whether to select Enable OPA Plug-in.
ASM integrates Open Policy Agent (OPA) to implement fine-grained access control for your applications. For example, using OPA for cross-microservice authorization. After selecting the Enable OPA Plug-in, just like the Istio Envoy proxy container, the OPA container will also be injected into the business pod. Then, you may use OPA to define access control policies in ASM to provide the out-of-the-box capability for distributed application developers and help them quickly define use policies and improve the development efficiency.
9) Service Agreement: Understand and accept Service Agreement and read and agree with ASM Service Terms and Disclaimer. Then, select this option.
10) Finally, click OK to begin creating an instance.
Note: It takes about 2 to 3 minutes to create an ASM instance.

56 posts | 8 followers
FollowXi Ning Wang(王夕宁) - June 16, 2020
Alibaba Cloud Native - September 8, 2022
Alibaba Container Service - May 23, 2025
Alibaba Container Service - August 30, 2024
Alibaba Container Service - May 23, 2025
feuyeux - December 30, 2020

56 posts | 8 followers
Follow Server Load Balancer
Server Load Balancer
Respond to sudden traffic spikes and minimize response time with Server Load Balancer
Learn More Container Service for Kubernetes
Container Service for Kubernetes
Alibaba Cloud Container Service for Kubernetes is a fully managed cloud container management service that supports native Kubernetes and integrates with other Alibaba Cloud products.
Learn More ACK One
ACK One
Provides a control plane to allow users to manage Kubernetes clusters that run based on different infrastructure resources
Learn More ApsaraDB for MyBase
ApsaraDB for MyBase
ApsaraDB Dedicated Cluster provided by Alibaba Cloud is a dedicated service for managing databases on the cloud.
Learn MoreMore Posts by Xi Ning Wang(王夕宁)