DDoS (Distributed Denial of Service) uses a large number of valid requests to consume lots of network resources and make services unresponsive and unavailable to legitimate users. Currently, DDoS attack is one of the most powerful cyber-attacks that are hard to defend against.
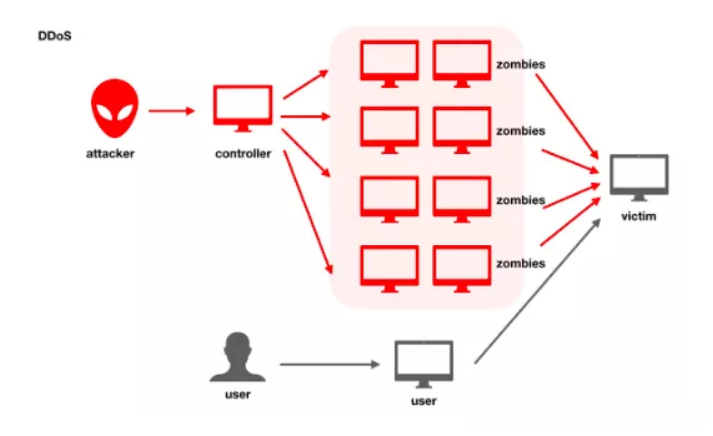
DDoS has been around the cybersecurity world for a long time and is an old attack method. DDoS prevention has also undergone different stages.
In the early days, no professional traffic scrubbing services were available to guard against DDoS attacks. At the time, the Internet bandwidth was also relatively smaller, and most people were using 56K modems to obtain dial-up Internet access. Only a small portion of the bandwidth can be exploited by attackers. Generally, defenders can prevent DDoS attacks simply by optimizing kernel parameters and iptables. People who can develop kernel can also improve the protection capability by writing kernel protection modules.
In this phase, features built in Linux can basically defend against DDoS attacks. For example, for SYN flood attacks, adjust the net.ipv4.tcp_max_syn_backlog parameter, control the upper limit of the syn queue to avoid full connections, and adjust net.ipv4.tcp_tw_recycle and net.ipv4.tcp_fin_timeout to make TCP retain the number of connection in TIME-WAIT and FIN-WAIT-2; for ICMP flood attacks, adjust Iptables to close or limit the rate of pinging packets, or filter malformed packets that are not compliant with the RFC protocol. However, this protection method only optimizes one single server. As the intensity of resource attacks increases, this protection method cannot efficiently defend against DDoS attacks.
Professional anti-DDoS hardware firewalls optimize power dissipation, forwarding chips, operating systems, and many other parts and can meet the requirement of DDoS traffic scrubbing. Generally, IDC service providers buy anti-DDoS hardware firewalls and deploy them at the entry of data centers to provide scrubbing services for the entire data centers. The performance of these scrubbing services gradually evolves from the original 100 MB per machine to 1 Gbit/s, 10 Gbit/s, 20 Gbit/s, 100 Gbit/s or higher. These scrubbing services basically cover various attacks from layer 3 to layer 7 (such as SYN-FLOOD, UDP-FLOOD, ICMP-FLOOD, ACK-FLOOD, TCP connection flood, CC attacks, DNS-FLOOD, and reflection attacks).
However, this DDoS prevention method is very costly for IDC service providers. Scrubbing devices are required at the entry of each data center and special maintenance officers are needed to maintain devices and services. In addition, not all IDCs have equal scrubbing and protection capabilities. Uplinks of some small data centers may only have 20 GB bandwidth and cannot reuse these scrubbing devices.
In the cloud era, services are deployed on various clouds or in traditional IDCs. The DDoS scrubbing services provided do not have a consistent standard. In the case of super-large amounts of DDoS attack traffic, data centers where services are hosted cannot provide matching protection capabilities. To protect services from being affected, we have to create the "black hole" concept. After the black hole mechanism is adopted, when a server has attack traffic that is more than the black hole triggering threshold in the IDC, the IDC will block Internet access for that server to avoid persistent attacks and ensure the overall stability of the IDC.
In this case, advanced anti-DDoS systems with secure IP addresses provide a complete set of anti-DDoS solutions by enabling high bandwidth for the whole data centers, converts traffic to these IP addresses and then forwards scrubbed traffic to users' source stations. This protection method supports the reuse of data center resources and allows data centers to focus more on their intended role. Additionally, this protection method simplifies DDoS prevention by providing DDoS scrubbing services in a SaaS-based manner.

Advanced anti-DDoS systems with secure IP addresses in the era of cloud can meet the requirement of high bandwidth. It also allows users to hide their source stations and flexibly change scrubbing service providers.
Bandwidth and network are the first requirement to implement DDoS protection. To efficiently defend against DDoS attacks, the first thing that we need to do is establish a data center with high bandwidth. Currently, the mainstream data centers in China are single-line data centers (having only one network provider, either China Telecom, China Unicom or China Mobile) and multi-line BGP data centers (having more than one network providers).
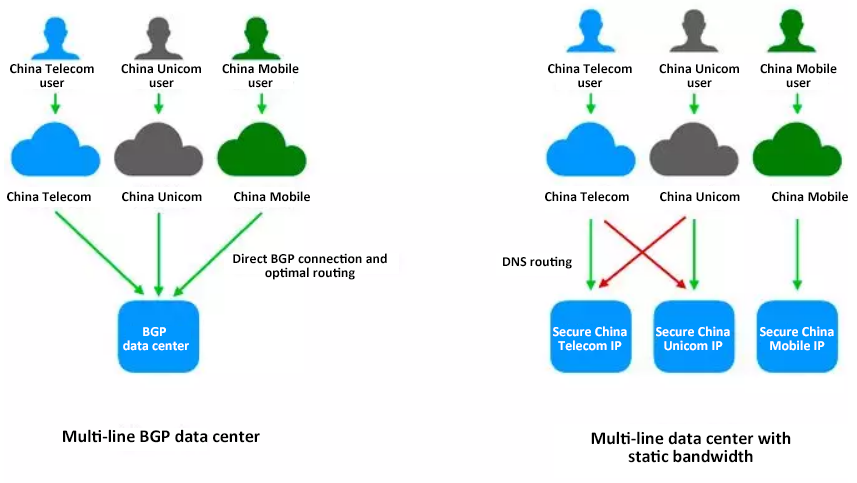
What are the characteristics of single-line data centers and multi-line BGP data centers and what are the differences between them?
Characteristics:
Another dimension is the maximum bandwidth. At present, 300 Gbit/s is just a basic protection capability. Protection level up to 1 Tbit/s or unlimited protection solutions become a choice for more and more users.
TB-level protection capability in multi-line BGP data centers also becomes one of the future development objectives. Alibaba Cloud is dedicated to providing customers with Anti-DDoS Pro that is excellent in both the access quality and protection capability.
This is another key technology. The core part of DDoS scrubbing is the interception of attack traffic. The following are the general attack types and countermeasures:
Attack Prevention
When sufficient bandwidth is available, we need to consider how to scrub DDoS attack traffic. Generally, professional DDoS scrubbing devices adopt the following typical protection and prevention methods: discarding malformed packets and specific protocols; verifying source reflection attacks; and statistics rate limit and behavior recognition. Attacks generally include SYN-FLOOD, UDP-FLOOD, ICMP-FLOOD, ACK-FLOOD, TCP connection flood, CC attacks, DNS-FLOOD, and reflection attacks.
Cluster Architecture
Judging from the current DDoS prevention trend, DDoS prevention solutions require elastic scaling to better defend against attacks. Here we need to mention the popularity of the 100 GB interface. Generally, hashing for traffic load balancing is based on the feature of the 5-tuple. If a single interface has relatively low bandwidth (say, 10 GB or 40 GB). If the hash of the 5-tuple for attack traffic is uneven, congestion is more likely to occur. Traffic will not be sent to scrubbing engines at all. This is also an important part of the big cluster cleaning system.
Preventive Defense Planning
It is also very important to plan countermeasures to defend against DDoS attacks. Efficient planning requires years of DDoS prevention experience. In the case of new attacks and emergency incidents, quick analysis and decision making play a critical role in solving problems.
Load balancing is a critical technology for advanced proxy protection. Load balancing includes layer-4 and layer-7 load balancing.
Layer-4 load balancing provides an exclusive IP address for each customer's business. Layer-4 server load balancing itself requires the high-performance and high-availability forwarding capability as well as the secure protection capability to defend against connection attacks.
Layer-7 load balancing targets proxy protection for website services. The support for HTTP/HTTPS and defense against CC attacks are integrated in the Layer-7 load balancing system.
To implement ultimate DDoS protection, it is necessary to combine in-depth security capability development in layer 4 and layer 7 with large traffic scrubbing clusters.
First, let's look at the data source. Currently many data source mechanisms are available. One well-known mechanism is to use NetFlow for sample analysis and attack detection. 1:1 traffic splitting can also be used to obtain all traffic for statistics and detection. Obviously, the latter method requires more resources and a more efficient data analysis system. Systems that require more development and technical support generally enable better analysis effectiveness.
After obtaining original messages and data, we need to differentiate applications. Application differentiation can be made at the IP level, IP+port level, domain name level or other levels. Different services require different prevention methods. We need to customize specialized prevention plans based on the characteristics of a specific service.
Current DDoS attack analysis no longer depends on statistics-based analysis algorithms. The theories and practices of behavior recognition and machine learning have been introduced for attack analysis. These algorithms can help us better defend against DDoS attacks. We should also consider how to efficiently apply these algorithms in users' attack protection efforts.
The preceding content reflects the Wooden Bucket Theory on DDoS attack protection: Each aspect of attack prevention will affect the overall protection effectiveness and efficiency. Future advanced anti-DDoS systems with secure IP addresses should feature elastic bandwidth, high redundancy, high availability, high access quality, and simple business integration. At the same time, the combination of OPENAPI-based DDoS protection and users' automatic maintenance systems can bring higher security to business and facilitate the business growth.

2,593 posts | 791 followers
FollowAlibaba Clouder - June 12, 2019
Neel_Shah - November 14, 2025
Alibaba Cloud Indonesia - January 8, 2025
Alibaba Clouder - June 12, 2019
Kidd Ip - November 24, 2025
Alibaba Clouder - January 12, 2021

2,593 posts | 791 followers
FollowLearn More
 Anti-DDoS
Anti-DDoS
A comprehensive DDoS protection for enterprise to intelligently defend sophisticated DDoS attacks, reduce business loss risks, and mitigate potential security threats.
Learn More WAF(Web Application Firewall)
WAF(Web Application Firewall)
A cloud firewall service utilizing big data capabilities to protect against web-based attacks
Learn MoreMore Posts by Alibaba Clouder